200-125 Exam Answer Part 1.2 – CCNA Cisco Certified Network Associate CCNA (v3.0)
101. Before installing a new, upgraded version of the IOS, what should be checked on the router, and which command should be used to gather this information? (Choose two.)
A. the amount of available ROM
B. the amount of available flash and RAM memory
C. the version of the bootstrap software present on the router D. show version
D. show processes
E. show running-config
Explanation/Reference:
When upgrading new version of the IOS we need to copy the IOS to the Flash so first we have to check if the Flash has enough memory or not. Also running the new IOS may require more RAM than the older one so we should check the available RAM too. We can check both with the “show version” command.
102. Which command reveals the last method used to powercycle a router?
A. show reload
B. show boot
C. show running-config
D. show version
Explanation/Reference:
The “show version” command can be used to show the last method to powercycle (reset) a router
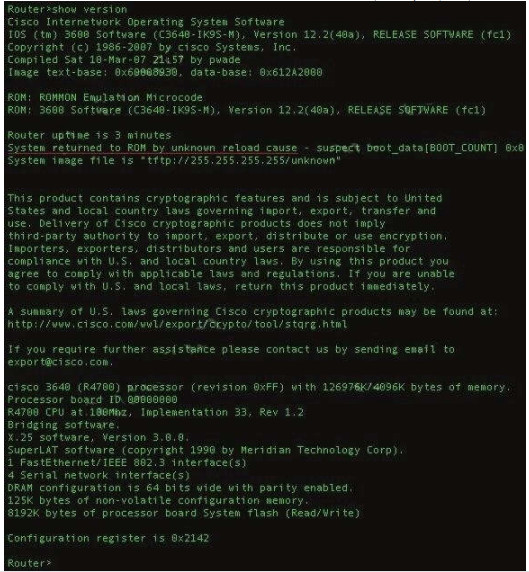
103. Which command would you use on a Cisco router to verify the Layer 3 path to a host?
A. tracert address
B. traceroute address
C. telnet address
D. ssh address
Explanation/Reference:
In computing, traceroute is a computer network diagnostic tool for displaying the route (path) and measuring transit delays of packets across an Internet Protocol (IP) network. The history of the route is recorded as the round-trip times of the packets received from each successive host (remote node) in the route (path); the sum of the mean times in each hop indicates the total time spent to establish the connection. Traceroute proceeds unless all (three) sent packets are lost more than twice, then the connection is lost and the route cannot be evaluated. Ping, on the other hand, only computes the final round-trip times from the destination point.
104. What information does a router running a link-state protocol use to build and maintain its topological database? (Choose two.)
A. hello packets
B. SAP messages sent by other routers
C. LSAs from other routers
D. beacons received on point-to-point links
E. routing tables received from other link-state routers
F. TTL packets from designated routers
Explanation/Reference:
Neighbor discovery is the first step in getting a link state environment up and running. In keeping with the friendly neighbor terminology, a Hello protocol is used for this step. The protocol will define a Hello packet format and a procedure for exchanging the packets and processing the information the packets contain.
After the adjacencies are established, the routers may begin sending out LSAs. As the term flooding implies, the advertisements are sent to every neighbor. In turn, each received LSA is copied and forwarded to every neighbor except the one that sent the LSA.
105. Refer to the exhibit. The Lakeside Company has the internetwork in the exhibit. The administrator would like to reduce the size of the routing table on the Central router. Which partial routing table entry in the Central router represents a route summary that represents the LANs in Phoenix but no additional subnets?
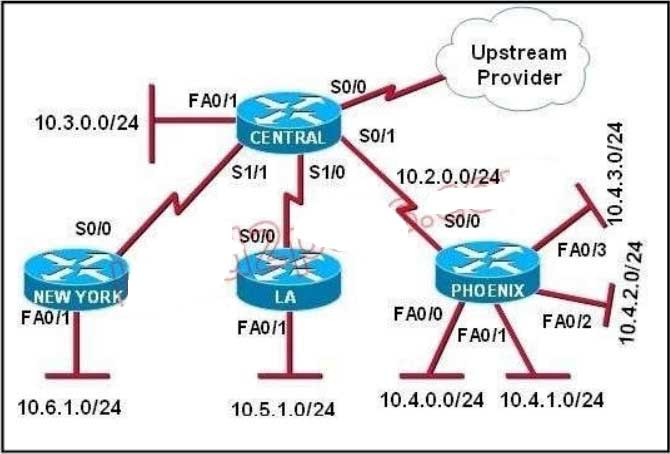
A. 10.0.0.0/22 is subnetted, 1 subnets
D 10.0.0.0 [90/20514560] via 10.2.0.2, 6w0d, Serial0/1
B. 10.0.0.0/28 is subnetted, 1 subnets
D 10.2.0.0 [90/20514560] via 10.2.0.2, 6w0d, Serial0/1
C. 10.0.0.0/30 is subnetted, 1 subnets
D 10.2.2.0 [90/20514560] via 10.2.0.2, 6w0d, Serial0/1
D. 10.0.0.0/22 is subnetted, 1 subnets
D 10.4.0.0 [90/20514560] via 10.2.0.2, 6w0d, Serial0/1
E. 10.0.0.0/28 is subnetted, 1 subnets
D. 10.4.4.0 [90/20514560] via 10.2.0.2, 6w0d, Serial0/1
F. 10.0.0.0/30 is subnetted, 1 subnets
D 10.4.4.4 [90/20514560] via 10.2.0.2, 6w0d, Serial0/1
Explanation/Reference:
The 10.4.0.0/22 route includes 10.4.0.0/24, 10.4.1.0/24, 10.4.2.0/24 and 10.4.3.0/24 only.
106. Refer to the graphic. A static route to the 10.5.6.0/24 network is to be configured on the HFD router. Which
commands will accomplish this? (Choose two.)
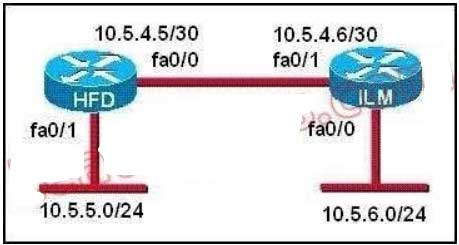
A. HFD(config)# ip route 10.5.6.0 0.0.0.255 fa0/0
B. HFD(config)# ip route 10.5.6.0 0.0.0.255 10.5.4.6
C. HFD(config)# ip route 10.5.6.0 255.255.255.0 fa0/0
D. HFD(config)# ip route 10.5.6.0 255.255.255.0 10.5.4.6
E. HFD(config)# ip route 10.5.4.6 0.0.0.255 10.5.6.0
F. HFD(config)# ip route 10.5.4.6 255.255.255.0 10.5.6.0
Explanation/Reference:
The simple syntax of static route: ip route destination-network-address subnet-mask {next-hop-IP-address | exit-interface} + destination-network-address: destination network address of the remote network + subnet mask: subnet mask of the destination network + next-hop-IP-address: the IP address of the receiving interface on the next-hop router + exit-interface: the local interface of this router where the packets will go out In the statement “ip route 10.5.6.0 255.255.255.0 fa0/0:
+ 10.5.6.0 255.255.255.0: the destination network
+fa0/0: the exit-interface
107. Which statements describe the routing protocol OSPF? (Choose three.)
A. It supports VLSM.
B. It is used to route between autonomous systems.
C. It confines network instability to one area of the network.
D. It increases routing overhead on the network.
E. It allows extensive control of routing updates.
F. It is simpler to configure than RIP v2.
Explanation/Reference:
The OSPF protocol is based on link-state technology, which is a departure from the Bellman-Ford vector based algorithms used in traditional Internet routing protocols such as RIP. OSPF has introduced new concepts such as authentication of routing updates, Variable Length Subnet Masks (VLSM), route summarization, and so forth.
OSPF uses flooding to exchange link-state updates between routers. Any change in routing information is flooded to all routers in the network. Areas are introduced to put a boundary on the explosion of link-state updates. Flooding and calculation of the Dijkstra algorithm on a router is limited to changes within an area.
108. Refer to the exhibit. A network administrator configures a new router and enters the copy startupconfig running-config command on the router. The network administrator powers down the router and sets it up at a remote location. When the router starts, it enters the system configuration dialog as shown. What is the cause of the problem?
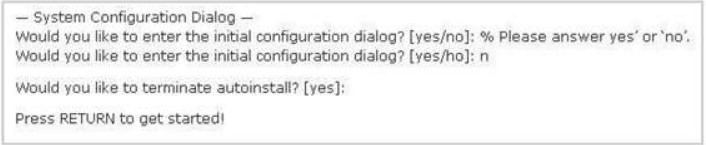
A. The network administrator failed to save the configuration.
B. The configuration register is set to 0x2100.
C. The boot system flash command is missing from the configuration.
D. The configuration register is set to 0x2102.
E. The router is configured with the boot system startup command.
Explanation/Reference:
The “System Configuration Dialog” appears only when no startup configuration file is found. The network administrator has made a mistake because the command “copy startup-config running- config” will copy the startup config (which is empty) over the running config (which is configured by the administrator). So everything configured was deleted. Note: We can tell the router to ignore the start-up configuration on the next reload by setting the register to 0?142. This will make the “System Configuration Dialog” appear at the next reload.
109. Refer to the exhibit. Which WAN protocol is being used?
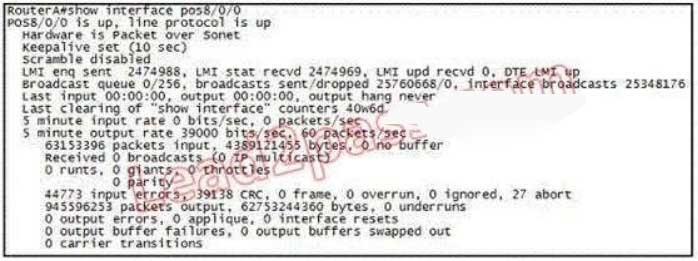
A. ATM
B. HDLC
C. Frame-relay
D. PPP
Explanation/Reference:
This question is to examine the show int command. According to the information provided in the exhibit, we can know that the data link protocol used in this network is the Frame Relay protocol. “LMI enq sent…”
110. What is the default administrative distance of OSPF?
A. 90
B. 100
C. 110
D. 120
Explanation/Reference:
Administrative distance is the feature that routers use in order to select the best path when there are two or more different routes to the same destination from two different routing protocols. Administrative distance defines the reliability of a routing protocol. Each routing protocol is prioritized in order of most to least reliable (believable) with the help of an administrative distance value. Default Distance Value Table This table lists the administrative distance default values of the protocols that Cisco supports:
Route Source
Default Distance Values
Connected interface
Static route
Enhanced Interior Gateway Routing Protocol (EIGRP) summary route External Border Gateway Protocol
(BGP)
Internal EIGRP
IGRP
OSPF
Intermediate System-to-Intermediate System (IS-IS)
Routing Information Protocol (RIP)
Exterior Gateway Protocol (EGP)
On Demand Routing (ODR)
External EIGRP
Internal BGP
Unknown*
111. Which characteristics are representative of a link-state routing protocol? (Choose three.)
A. provides common view of entire topology
B. exchanges routing tables with neighbors
C. calculates shortest path
D. utilizes event-triggered updates
E. utilizes frequent periodic updates
Explanation/Reference:
Each of routers running link-state routing protocol learns paths to all the destinations in its “area” so we can say although it is a bit unclear.
Link-state routing protocols generate routing updates only (not the whole routing table) when a change occurs in the network topology so Link-state routing protocol like OSPF uses Dijkstra algorithm to calculate the shortest path -> . Unlike
Distance vector routing protocol (which utilizes frequent periodic updates), link-state routing protocol utilizes event-triggered updates (only sends update when a change occurs) ->
112. Which command would you configure globally on a Cisco router that would allow you to view directly connected Cisco devices?
A. enable cdp
B. cdp enable
C. cdp run
D. run cdp
Explanation/Reference:
CDP is enabled on Cisco routers by default. If you prefer not to use the CDP capability, disable it with the no cdp run command. In order to reenable CDP, use the cdp run command in global configuration mode. The “cdp enable” command is an interface command, not global.
113. Refer to the exhibit. According to the routing table, where will the router send a packet destined for 10.1.5.65?
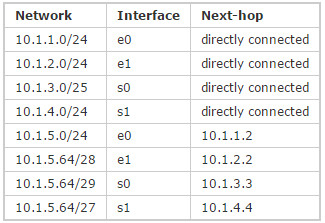
A. 10.1.1.2
B. 10.1.2.2
C. 10.1.3.3
D. 10.1.4.4
Explanation/Reference:
The destination IP address 10.1.5.65 belongs to 10.1.5.64/28, 10.1.5.64/29 & 10.1.5.64/27 subnets but the “longest prefix match” algorithm will choose the most specific subnet mask -> the prefix “/29 will be chosen to route the packet. Therefore the next-hop should be 10.1.3.3 -> .
114. Refer to the exhibit. Which address and mask combination represents a summary of the routes learned by EIGRP?
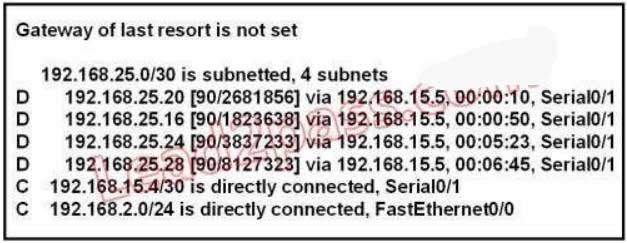
A. 192.168.25.0 255.255.255.240
B. 192.168.25.0 255.255.255.252
C. 192.168.25.16 255.255.255.240
D. 192.168.25.16 255.255.255.252
E. 192.168.25.28 255.255.255.240
F. 192.168.25.28 255.255.255.252
Explanation/Reference:
The binary version of 20 is 10100.
The binary version of 16 is 10000.
The binary version of 24 is 11000.
The binary version of 28 is 11100.
The subnet mask is /28. The mask is 255.255.255.240.
Note: From the output above, EIGRP learned 4 routes and we need to find out the summary of them:
+ 192.168.25.16
+ 192.168.25.20
+ 192.168.25.24
+ 192.168.25.28
-> The increment should bE. 28 ?16 = 12 but 12 is not an exponentiation of 2 so we must choose 16 (24).
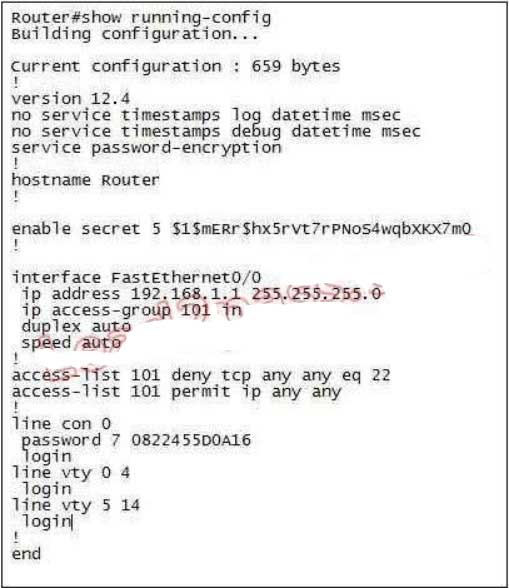
Therefore the subnet mask is /28 (=1111 1111.1111 1111.1111 1111.11110000) = 255.255.255.240
So the best answer should be 192.168.25.16 255.255.255.240
115. Refer to the exhibit. Assuming that the entire network topology is shown, what is the operational status of the interfaces of R2 as indicated by the command output shown?
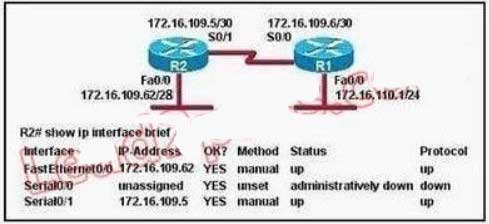
A. One interface has a problem.
B. Two interfaces have problems.
C. The interfaces are functioning correctly.
D. The operational status of the interfaces cannot be determined from the output shown.
Explanation/Reference:
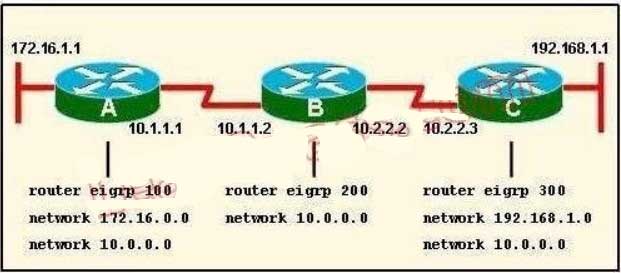
The output shown shows normal operational status of the router’s interfaces. Serial0/0 is down because it has been disabled using the “shutdown” command.
116. Which two locations can be configured as a source for the IOS image in the boot system command? (Choose two.)
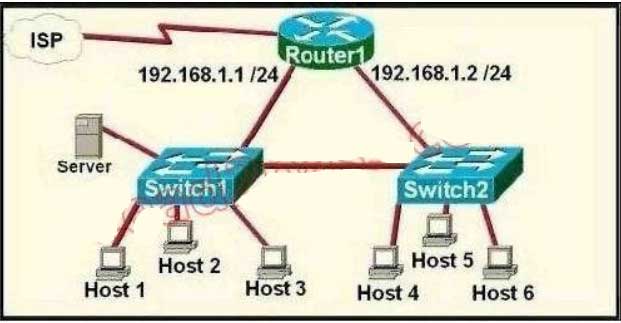
A. RAM
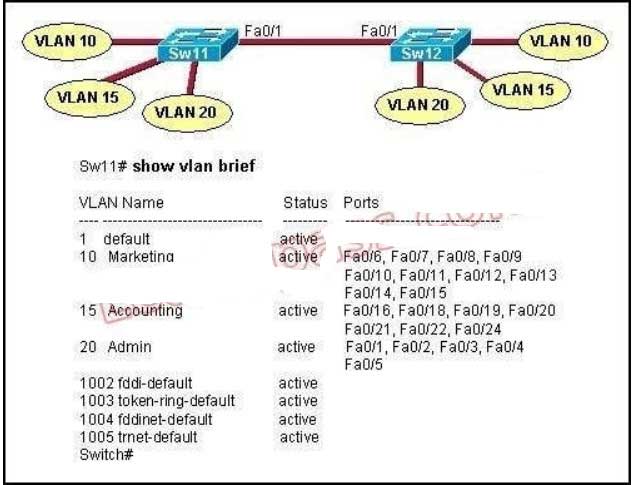
B. NVRAM
C. flash memory
D. HTTP server
E. TFTP server
F. Telnet server
Explanation/Reference:
The following locations can be configured as a source for the IOS image:
+ Flash (the default location)
+ TFTP server
+ ROM (used if no other source is found)
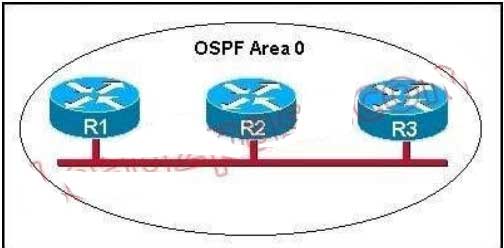
117. Refer to the exhibit. Given the output for this command, if the router ID has not been manually set, what router ID will OSPF use for this router?
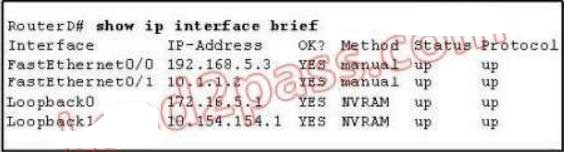
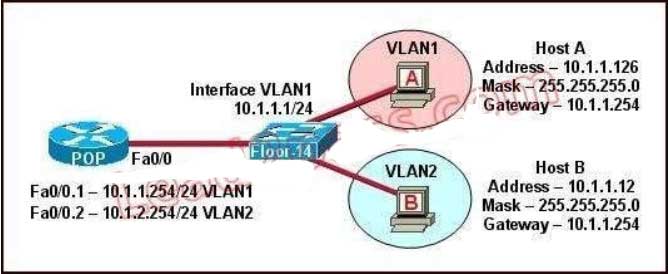
A. 10.1.1.2
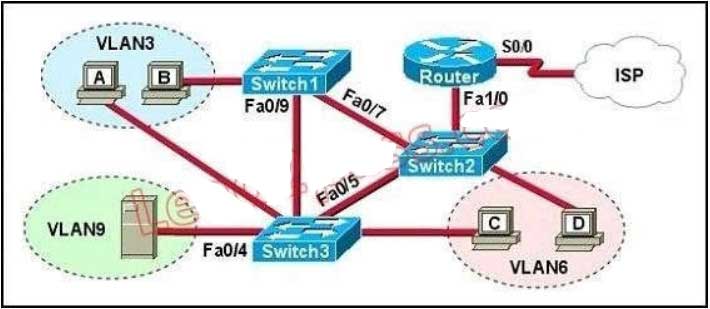
B. 10.154.154.1
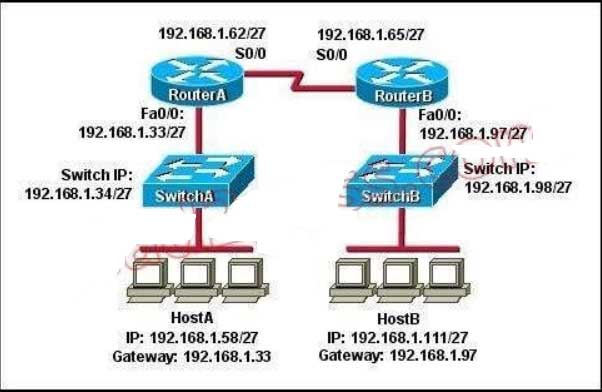
C. 172.16.5.1
D. 192.168.5.3
Explanation/Reference:
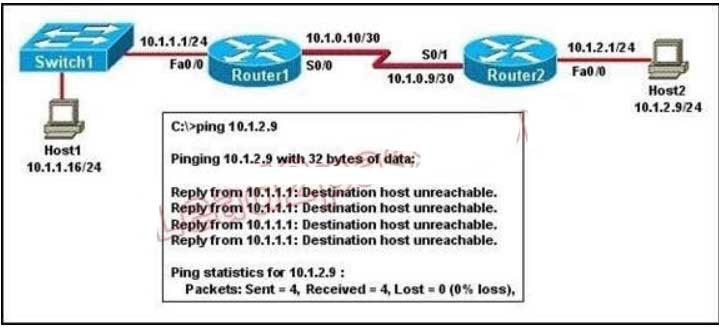
The highest IP address of all loopback interfaces will be chosen -> Loopback 0 will be chosen as the router
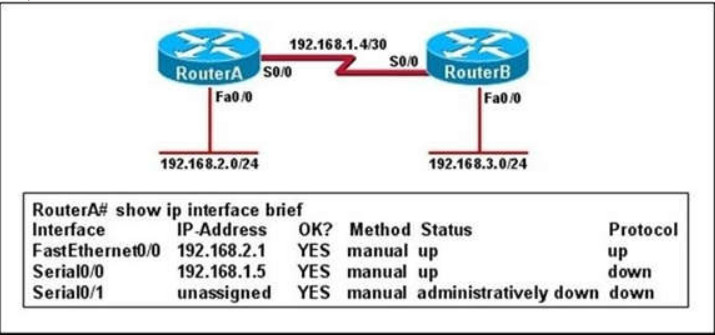
ID.
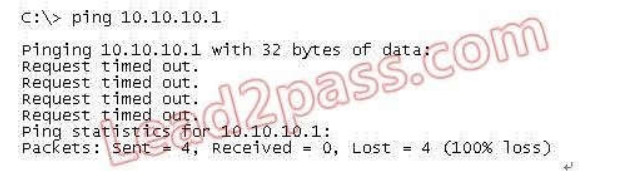
118. Refer to the exhibit. Based on the exhibited routing table, how will packets from a host within the 192.168.10.192/26 LAN be forwarded to 192.168.10.1?
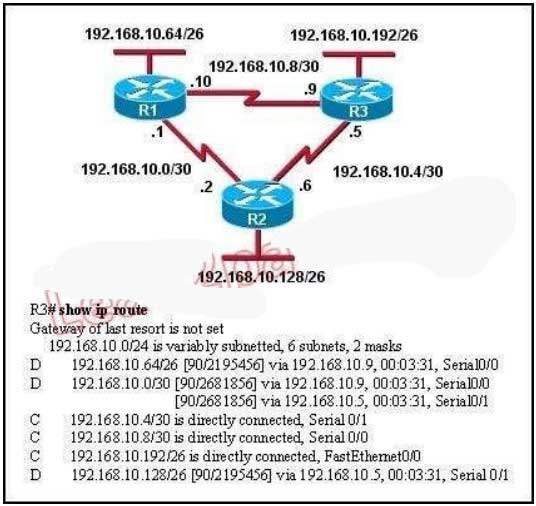
A. The router will forward packets from R3 to R2 to R1.
B. The router will forward packets from R3 to R1 to R2.
C. The router will forward packets from R3 to R2 to R1 AND from R3 to R1.
D. The router will forward packets from R3 to R1.
Explanation/Reference:
From the routing table we learn that network 192.168.10.0/30 is learned via 2 equal-cost paths (192.168.10.9 &192.168.10.5) -> traffic to this network will be load-balancing.
119. Refer to the exhibit. C-router is to be used as a “router-on-a-stick” to route between the VLANs. All the interfaces have been properly configured and IP routing is operational. The hosts in the VLANs have been configured with the appropriate default gateway. What is true about this configuration?
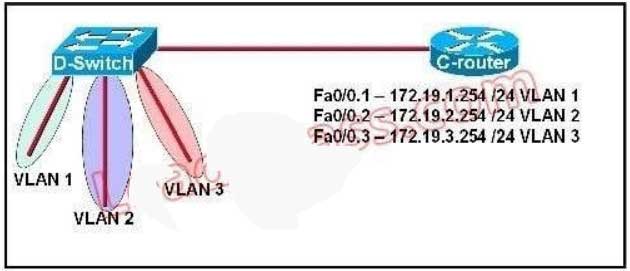
A. These commands need to be added to the configuration:
C-router(config)# router eigrp 123
C-router(config-router)# network 172.19.0.0
B. These commands need to be added to the configuration:
C-router(config)# router ospf 1
C-router(config-router)# network 172.19.0.0 0.0.3.255 area 0
C. These commands need to be added to the configuration:
C-router(config)# router rip
C-router(config-router)# network 172.19.0.0
D. No further routing configuration is required.
120. Which two statements describe the process identifier that is used in the command to configure OSPF on a router? (Choose two.) Router(config)# router ospf 1
A. All OSPF routers in an area must have the same process ID
B. Only one process number can be used on the same router.
C. Different process identifiers can be used to run multiple OSPF processes
D. The process number can be any number from 1 to 65,535.
E. Hello packets are sent to each neighbor to determine the processor identifier.
Explanation/Reference:
Multiple OSPF processes can be configured on a router using multiple process ID’s.
The valid process ID’s are shown below:
Edge-B(config)#router ospf ?
<1-65535> Process ID
122. Refer to the exhibit. What commands must be configured on the 2950 switch and the router to allow communication between host 1 and host 2? (Choose two.)
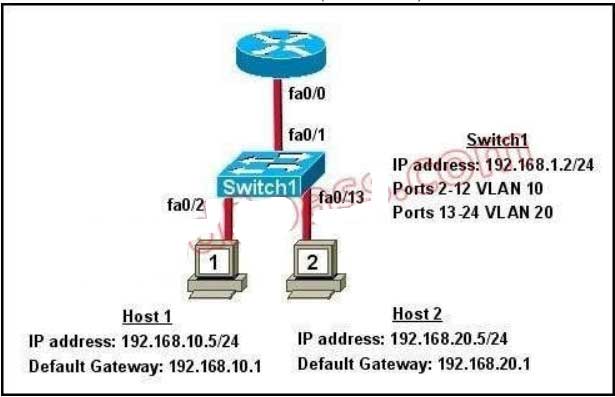
A. Router(config)# interface fastethernet 0/0
Router(config-if)# ip address 192.168.1.1 255.255.255.0 Router(config-if)#
no shut down
B. Router(config)# interface fastethernet 0/0
Router(config-if)# no shut down
Router(config)# interface fastethernet 0/0.1
Router(config-subif)# encapsulation dot1q 10
Router(config-subif)# ip address 192.168.10.1 255.255.255.0
Router(config)# interface fastethernet 0/0.2
Router(config-subif)# encapsulation dot1q 20
Router(config-subif)# ip address 192.168.20.1 255.255.255.0
C. Router(config)# router eigrp 100
Router(config-router)# network 192.168.10.0
Router(config-router)# network 192.168.20.0
D. Switch1(config)# vlan database Switch1(config-vlan)# vtp domain XYZ
Switch1(config-vlan)# vtp server
E. Switch1(config)# interface fastethernet 0/1 Switch1(config-if)# switchport
mode trunk F. Switch1(config)# interface vlan 1 Switch1(config-if)# ip
default-gateway 192.168.1.1
Explanation/Reference:
The router will need to use subinterfaces, where each subinterface is assigned a VLAN and IP address for each VLAN. On the switch, the connection to the router need to be configured as a trunk using the switchport mode trunk command and it will need a default gateway for VLAN 1.
123. Refer to the exhibit. For what two reasons has the router loaded its IOS image from the location that is shown? (Choose two.)
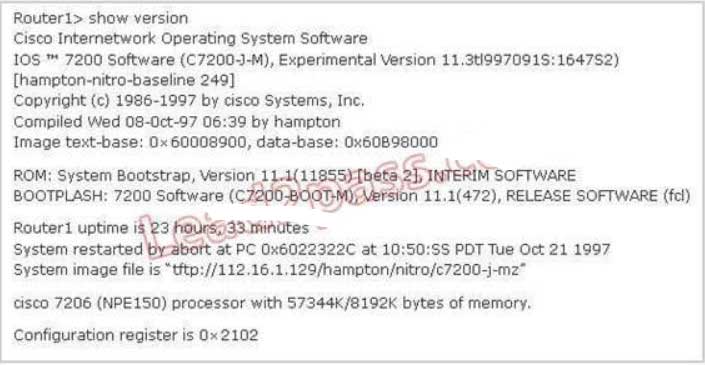
A. Router1 has specific boot system commands that instruct it to load IOS from a TFTP server.
B. Router1 is acting as a TFTP server for other routers.
C. Router1 cannot locate a valid IOS image in flash memory.
D. Router1 defaulted to ROMMON mode and loaded the IOS image from a TFTP server.
E. Cisco routers will first attempt to load an image from TFTP for management purposes
Explanation/Reference:
The loading sequence of CISCO IOS is as follows:
Booting up the router and locating the Cisco IOS
POST (power on self test)
Bootstrap code executed
Check Configuration Register value (NVRAM) which can be modified using the config-register
command
= ROM Monitor mode
= ROM IOS
– 15 = startup-config in NVRAM
4. Startup-config filE. Check for boot system commands (NVRAM) If boot system commands in startup-config a. Run boot system commands in order they appear in startup-config to locate the IOS b. [If boot system commands fail, use default fallback sequence to locate the IOS (Flash, TFTP, ROM)?] If no boot system commands in startup-config use the default fallback sequence in locating the IOS:
Flash (sequential)
TFTP server (netboot)
ROM (partial IOS) or keep retrying TFTP depending upon router model
5. If IOS is loaded, but there is no startup-config file, the router will use the default fallback sequence for
locating the IOS and then it will enter setup mode or the setup dialogue.
124. Refer to the exhibit. What can be determined about the router from the console output?
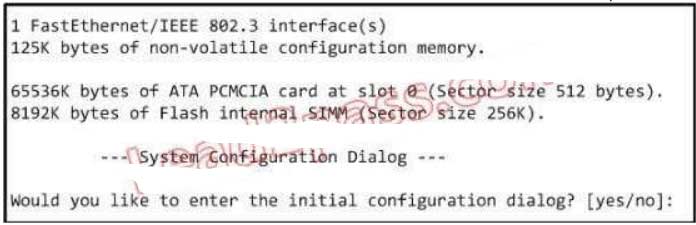
A. No configuration file was found in NVRAM.
B. No configuration file was found in flash.
C. No configuration file was found in the PCMCIA card.
D. Configuration file is normal and will load in 15 seconds.
Explanation/Reference:
When no startup configuration file is found in NVRAM, the System Configuration Dialog will appear to ask if we want to enter the initial configuration dialog or not.
125. Which three elements must be used when you configure a router interface for VLAN trunking? (Choose three.)
A. one physical interface for each subinterface
B. one IP network or subnetwork for each subinterface
C. a management domain for each subinterface
D. subinterface encapsulation identifiers that match VLAN tags
E. one subinterface per VLAN
F. subinterface numbering that matches VLAN tags
Explanation/Reference:
This scenario is commonly called a router on a stick. A short, well written article on this operation can be
found here: http://www.thebryantadvantage.com/RouterOnAStickCCNACertificationExamTutorial.htm
126. Which commands are required to properly configure a router to run OSPF and to add network 192.168.16.0/24 to OSPF area 0? (Choose two.)
A. Router(config)# router ospf 0
B. Router(config)# router ospf 1
C. Router(config)# router ospf area 0
D. outer(config-router)# network 192.168.16.0 0.0.0.255 0
E. Router(config-router)# network 192.168.16.0 0.0.0.255 area 0
F. Router(config-router)# network 192.168.16.0 255.255.255.0 area 0
Explanation/Reference:
In the router ospf command, the ranges from 1 to 65535 so o is an invalid number -> but To configure OSPF, we need a wildcard in the “network” statement, not a subnet mask. We also need to assgin an area to this process ->
127. A router receives information about network 192.168.10.0/24 from multiple sources. What will the router consider the most reliable information about the path to that network?
A. a directly connected interface with an address of 192.168.10.254/24
B. a static route to network 192.168.10.0/24
C. a RIP update for network 192.168.10.0/24
D. an OSPF update for network 192.168.0.0/16
E. a default route with a next hop address of 192.168.10.1
F. a static route to network 192.168.10.0/24 with a local serial interface configured as the next hop
Explanation/Reference:
When there is more than one way to reach a destination, it will choose the best one based on a couple of things. First, it will choose the route that has the longest match; meaning the most specific route. So, in this case the /24 routes will be chosen over the /16 routes. Next, from all the /24 routes it will choose the one with the lowest administrative distance. Directly connected routes have an AD of 1 so this will be the route
chosen.
128. What is the default maximum number of equal-cost paths that can be placed into the routing table of aCisco OSPF router?
A. 2
B. 4
C. 16
D. unlimited
Explanation/Reference:
maximum-paths (OSPF) To control the maximum number of parallel routes that Open Shortest Path First (OSPF) can support, use the maximum-paths command. Syntax Description maximum Maximum number of parallel routes that OSPF can install in a routing table. The range is from 1 to 16
routes.
Command Default
8 paths
129. Which command shows your active Telnet connections?
A. show cdp neigbors
B. show session
C. show users
D. show vty logins
Explanation/Reference:
The “show users” shows telnet/ssh connections to your router while “show sessions” shows telnet/ssh connections from your router (to other devices). The question asks about “your active Telnet connections”, meaning connections from your router so the answer should be A.
130. Refer to the exhibit. What statement is true of the configuration for this network?
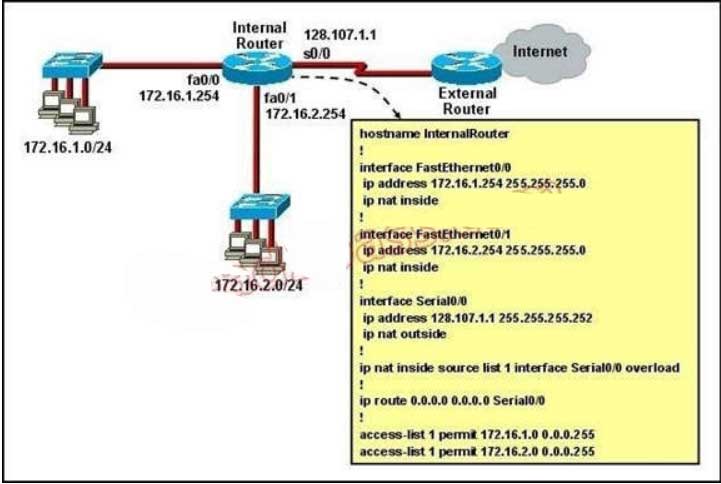
A. The configuration that is shown provides inadequate outside address space for translation of the
number of inside addresses that are supported.
B. Because of the addressing on interface FastEthernet0/1, the Serial0/0 interface address will not support
the NAT configuration as shown.
C. The number 1 referred to in the ip nat inside source command references access-list number 1.
D. ExternalRouter must be configured with static routes to networks 172.16.1.0/24 and 172.16.2.0/24.
131. Which type of EIGRP route entry describes a feasible successor?
A. a backup route, stored in the routing table
B. a primary route, stored in the routing table
C. a backup route, stored in the topology table
D. a primary route, stored in the topology table
Explanation/Reference:
EIGRP uses the Neighbor Table to list adjacent routers. The Topology Table list all the learned routers to destination whilst the Routing Table contains the best route to a destination, which is known as the Successor. The Feasible Successor is a backup route to a destination which is kept in the Topology Table.
132. Which statement describes the process of dynamically assigning IP addresses by the DHCP server?
A. Addresses are allocated after a negotiation between the server and the host to determine the length of
the agreement.
B. Addresses are permanently assigned so that the hosts uses the same address at all times.
C. Addresses are assigned for a fixed period of time, at the end of the period, a new request for an
address must be made.
D. Addresses are leased to hosts, which periodically contact the DHCP server to renew the lease.
133. What are two benefits of using NAT? (Choose two.)
A. NAT facilitates end-to-end communication when IPsec is enabled.
B. NAT eliminates the need to re-address all hosts that require external access.
C. NAT conserves addresses through host MAC-level multiplexing.
D. Dynamic NAT facilitates connections from the outside of the network.
E. NAT accelerates the routing process because no modifications are made on the packets
F. NAT protects network security because private networks are not advertised.
Explanation/Reference:
By not revealing the internal Ip addresses, NAT adds some security to the inside network -> F is correct.
NAT has to modify the source IP addresses in the packets -> E is not correct.
Connection from the outside of the network through a “NAT” network is more difficult than a more network because IP addresses of inside hosts are hidden -> C is not correct.
In order for IPsec to work with NAT we need to allow additional protocols, including Internet Key Exchange
(IKE), Encapsulating Security Payload (ESP) and Authentication Header (AH) -> more complex -> A is not
correct.
By allocating specific public IP addresses to inside hosts, NAT eliminates the need to re-address the inside
hosts -> B is correct.
NAT does conserve addresses but not through host MAC-level multiplexing. It conserves addresses by allowing many private IP addresses to use the same public IP address to go to the Internet -> C is not correct.
134. On which options are standard access lists based?
A. destination address and wildcard mask
B. destination address and subnet mask
C. source address and subnet mask
D. source address and wildcard mask
Explanation/Reference:
Standard ACL’s only examine the source IP address/mask to determine if a match is made. Extended ACL’s examine the source and destination address, as well as port information.
135. A network engineer wants to allow a temporary entry for a remote user with a specific username and password so that the user can access the entire network over the Internet. Which ACL can be used?
A. standard
B. extended
C. dynamic
D. reflexive
Explanation/Reference:
We can use a dynamic access list to authenticate a remote user with a specific username and password.
The authentication process is done by the router or a central access server such as a TACACS+ or RADIUS server. The configuration of dynamic ACL can be read here: http://www.cisco.com/en/US/tech/tk583/tk822/technologies_tech_note09186a0080094524.shtml
136.How does a DHCP server dynamically assign IP addresses to hosts?
A. Addresses are permanently assigned so that the host uses the same address at all times.
B. Addresses are assigned for a fixed period of time. At the end of the period, a new request for an
address must be made, and another address is then assigned.
C. Addresses are leased to hosts. A host will usually keep the same address by periodically contacting thDHCP server to renew the lease.
D. Addresses are allocated after a negotiation between the server and the host to determine the length of
the agreement.
Explanation/Reference:
DHCP works in a client/server mode and operates like any other client/server relationship. When a PC connects to a DHCP server, the server assigns or leases an IP address to that PC. The PC connects to the network with that leased IP address until the lease expires. The host must contact the DHCP server periodically to extend the lease. This lease mechanism ensures that hosts that move or power off do not hold onto addresses that they do not need. The DHCP server returns these addresses to the address pool and reallocates them as necessary.
137. Refer to the exhibit. Which rule does the DHCP server use when there is an IP address conflict?

A. The address is removed from the pool until the conflict is resolved.
B. The address remains in the pool until the conflict is resolved.
C. Only the IP detected by Gratuitous ARP is removed from the pool
D. Only the IP detected by Ping is removed from the pool.
E. The IP will be shown, even after the conflict is resolved.
Explanation/Reference:
An address conflict occurs when two hosts use the same IP address. During address assignment, DHCP checks for conflicts using ping and gratuitous ARP. If a conflict is detected, the address is removed from the pool. The address will not be assigned until the administrator resolves the conflict.
http://www.cisco.com/en/US/docs/ios/12_1/iproute/configuration/guide/1cddhcp.html
138. Which two tasks does the Dynamic Host Configuration Protocol perform? (Choose two.)
A. Set the IP gateway to be used by the network.
B. Perform host discovery used DHCPDISCOVER message.
C. Configure IP address parameters from DHCP server to a host.
D. Provide an easy management of layer 3 devices.
E. Monitor IP performance using the DHCP server.
F. Assign and renew IP address from the default pool.
Explanation/Reference:
The Dynamic Host Configuration Protocol (DHCP) is a network protocol used to configure devices that are connected to a network (known as hosts) so they can communicate on that network using the Internet Protocol (IP). It involves clients and a server operating in a clientserver model. DHCP servers assigns IP addresses from a pool of addresses and also assigns other parameters such as DNS and default gateways to hosts.
139, Refer to the exhibit. What statement is true of the configuration for this network?
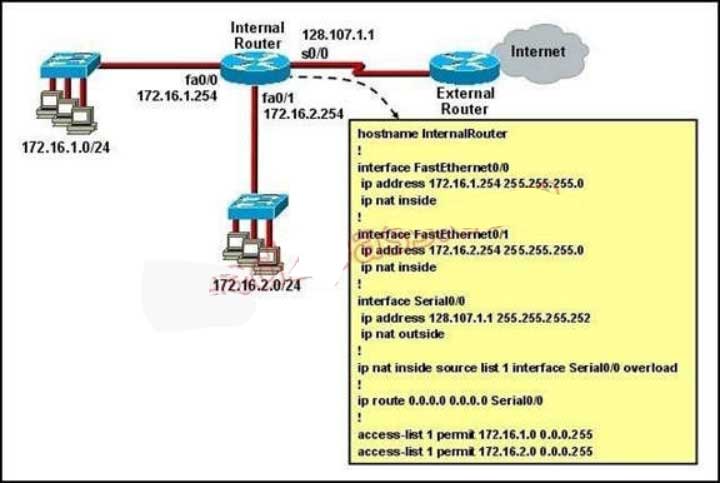
A. The configuration that is shown provides inadequate outside address space for translation of the
number of inside addresses that are supported.
B. Because of the addressing on interface FastEthernet0/1, the Serial0/0 interface address will not support the NAT configuration as shown.
C. The number 1 referred to in the ip nat inside source command references access-list number 1.
D. ExternalRouter must be configured with static routes to networks 172.16.1.0/24 and 172.16.2.0/24.
140. When a DHCP server is configured, which two IP addresses should never be assignable to hosts? (Choose two.)
A. network or subnetwork IP address
B. broadcast address on the network
C. IP address leased to the LAN
D. IP address used by the interfaces
E. manually assigned address to the clients
F. designated IP address to the DHCP server
Explanation/Reference:
Network or subnetwork IP address (for example 11.0.0.0/8 or 13.1.0.0/16) and broadcast address (for example 23.2.1.255/24) should never be assignable to hosts. When try to assign these addresses to hosts, you will receive an error message saying that they can’t be assignable.
141. Which two statements about static NAT translations are true? (Choose two.)
A. They allow connections to be initiated from the outside.
B. They require no inside or outside interface markings because addresses are statically defined.
C. They are always present in the NAT table.
D. They can be configured with access lists, to allow two or more connections to be initiated from the
outside.
Explanation/Reference:
Static NAT is to map a single outside IP address to a single inside IP address. This is typically done to allow incoming connections from the outside (Internet) to the inside. Since these are static, they are always present in the NAT table even if they are not actively in use.
142. Which statement about access lists that are applied to an interface is true?
A. You can place as many access lists as you want on any interface.
B. You can apply only one access list on any interface.
C. You can configure one access list, per direction, per Layer 3 protocol.
D. You can apply multiple access lists with the same protocol or in different directions.
Explanation/Reference:
We can have only 1 access list per protocol, per direction and per interface. It means: + We can not have 2 inbound access lists on an interface + We can have 1 inbound and 1 outbound access list on an interface
143. Which item represents the standard IP ACL?
A. access-list 110 permit ip any any
B. access-list 50 deny 192.168.1.1 0.0.0.255
C. access list 101 deny tcp any host 192.168.1.1
D. access-list 2500 deny tcp any host 192.168.1.1 eq 22
Explanation/Reference:
The standard access lists are ranged from 1 to 99 and from 1300 to 1999 so only access list 50 is a standard access list.
144. A network administrator is configuring ACLs on a Cisco router, to allow traffic from hosts on networks 192.168.146.0, 192.168.147.0, 192.168.148.0, and 192.168.149.0 only. Which two ACL statements, when combined, would you use to accomplish this task? (Choose two.)
A. access-list 10 permit ip 192.168.146.0 0.0.1.255
B. access-list 10 permit ip 192.168.147.0 0.0.255.255
C. access-list 10 permit ip 192.168.148.0 0.0.1.255
D. access-list 10 permit ip 192.168.149.0 0.0.255.255
E. access-list 10 permit ip 192.168.146.0 0.0.0.255
F. access-list 10 permit ip 192.168.146.0 255.255.255.0
Explanation/Reference:
access-list 10 permit ip 192.168.146.0 0.0.1.255 will include the 192.168.146.0 and 192.168.147.0 subnets, while access-list 10 permit ip 192.168.148.0 0.0.1.255 will include
145. What can be done to secure the virtual terminal interfaces on a router? (Choose two.)
A. Administratively shut down the interface.
B. Physically secure the interface.
C. Create an access list and apply it to the virtual terminal interfaces with the access-group command.
D. Configure a virtual terminal password and login process.
E. Enter an access list and apply it to the virtual terminal interfaces using the access-class command.
Explanation/Reference:
It is a waste to administratively shut down the interface. Moreover, someone can still access the virtual terminal interfaces via other interfaces -> We can not physically secure a virtual interface because it is “virtual” -> To apply an access list to a virtual terminal interface we must use the “access-class” command. The “access-group” command is only used to apply an access list to a physical interface -> C is not correct. The most simple way to secure the virtual terminal interface is to configure a username & password to prevent unauthorized login.
146. Which two commands correctly verify whether port security has been configured on port FastEthernet 0/12 on a switch? (Choose two.)
A. SW1#show port-secure interface FastEthernet 0/12
B. SW1#show switchport port-secure interface FastEthernet 0/12
C. SW1#show running-config
D. SW1#show port-security interface FastEthernet 0/12
E. SW1#show switchport port-security interface FastEthernet 0/12
Explanation/Reference:
We can verify whether port security has been configured by using the “show running-config” or “show port- security interface ” for more detail. An example of the output of “show port-security interface ” command is shown below:

147. Refer to the exhibit. The following commands are executed on interface fa0/1 of 2950Switch.
2950Switch(config-if)# switchport port-security
2950Switch(config-if)# switchport port-security mac-address sticky
2950Switch(config-if)# switchport port-security maximum 1
The Ethernet frame that is shown arrives on interface fa0/1.
What two functions will occur when this frame is received by 2950Switch? (Choose two.)
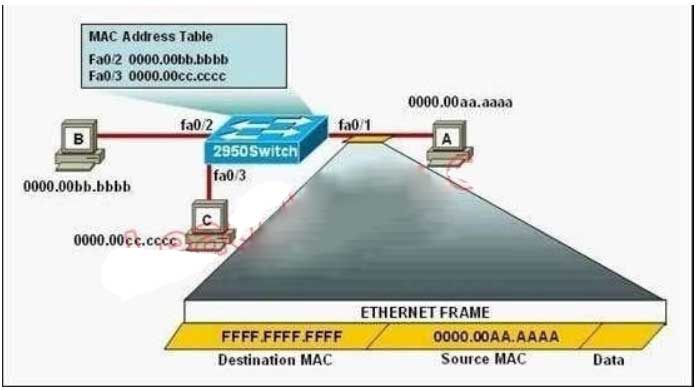
A. The MAC address table will now have an additional entry of fa0/1 FFFF.FFFF.FFFF.
B. Only host A will be allowed to transmit frames on fa0/1.
C. This frame will be discarded when it is received by 2950Switch.
D. All frames arriving on 2950Switch with a destination of 0000.00aa.aaaa will be forwarded out fa0/1.
E. Hosts B and C may forward frames out fa0/1 but frames arriving from other switches will not be
forwarded out fa0/1.
F. Only frames from source 0000.00bb.bbbb, the first learned MAC address of 2950Switch, will be
Explanation/Reference:
The configuration shown here is an example of port security, specifically port security using sticky addresses. You can use port security with dynamically learned and static MAC addresses to restrict a port’s ingress traffic by limiting the MAC addresses that are allowed to send traffic into the port. When you assign secure MAC addresses to a secure port, the port does not forward ingress traffic that has source addresses outside the group of defined addresses. If you limit the number of secure MAC addresses to one and assign a single secure MAC address, the device attached to that port has the full bandwidth of the port. Port security with sticky MAC addresses provides many of the same benefits as port security with static MAC addresses, but sticky MAC addresses can be learned dynamically. Port security with sticky MAC addresses retains dynamically learned MAC addresses during a link-down condition.
148. What will be the result if the following configuration commands are implemented on a Cisco switch?
Switch(config-if)# switchport port-security
Switch(config-if)# switchport port-security mac-address sticky
A. A dynamically learned MAC address is saved in the startup-configuration file.
B. A dynamically learned MAC address is saved in the running-configuration file.
C. A dynamically learned MAC address is saved in the VLAN database.
D. Statically configured MAC addresses are saved in the startup-configuration file if frames from that
address are received.
E. Statically configured MAC addresses are saved in the running-configuration file if frames from that
address are received.
Explanation/Reference:
In the interface configuration mode, the command switchport port-security mac-address sticky enables sticky learning. When entering this command, the interface converts all the dynamic secure MAC addresses to sticky secure MAC addresses.
149. The network administrator cannot connect to Switch1 over a Telnet session, although the hosts attached to Switch1 can ping the interface Fa0/0 of the router. Given the information in the graphic and assuming that the router and Switch2 are configured properly, which of the following commands should be issued on Switch1 to correct this problem?
A. Switch1(config)# line con0
Switch1(config-line)# password cisco
Switch1(config-line)#login
B. Switch1(config)# interface fa0/1
Switch1(config-if)# ip address 192.168.24.3 255.255.255.0
C. Switch1(config)# ip default-gateway 192.168.24.1
D. Switch1(config)# interface fa0/1
Switch1(config-if)# duplex full
Switch1(config-if)# speed 100
E. Switch1(config)# interface fa0/1
Switch1(config-if)# switchport mode trunk
Explanation/Reference:
Since we know hosts can reach the router through the switch, we know that connectivity, duplex. Speed, etc. are good. However, for the switch itself to reach networks outside the local one, the ip default-gateway command must be used.
150. Refer to the exhibit. Which of these statements correctly describes the state of the switch once the boot process has been completed?
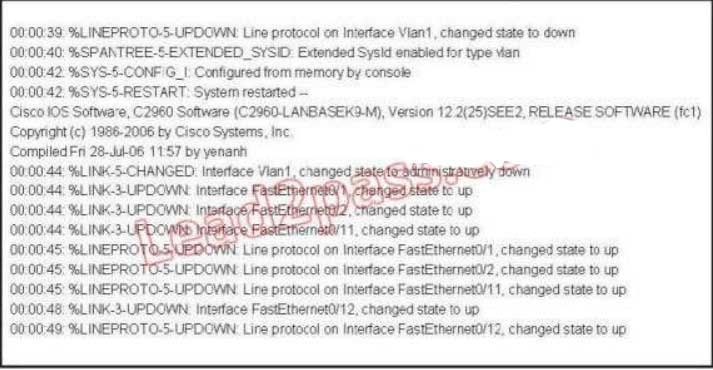
A. As FastEthernet0/12 will be the last to come up, it will be blocked by STP.
B. Remote access management of this switch will not be possible without configuration change.
C. More VLANs will need to be created for this switch.
D. The switch will need a different IOS code in order to support VLANs and STP.
Explanation/Reference:
Notice the line, which says “Interface VLAN1, changed state to administratively down”. This shows that VLAN1 is shut down. Hence remote management of this switch is not possible unless VLAN1 is brought back up. Since VLAN1 is the only interface shown in the output, you have to assume that no other VLAN interface has been configured with an IP Address.
151. Refer to exhibit. A network administrator cannot establish a Telnet session with the indicated router. What is the cause of this failure?
A. A Level 5 password is not set.
B. An ACL is blocking Telnet access.
C. The vty password is missing.
D. The console password is missing.
Explanation/Reference:
The login keyword has been set, but not password. This will result in the “password required, but none set” message to users trying to telnet to this router.
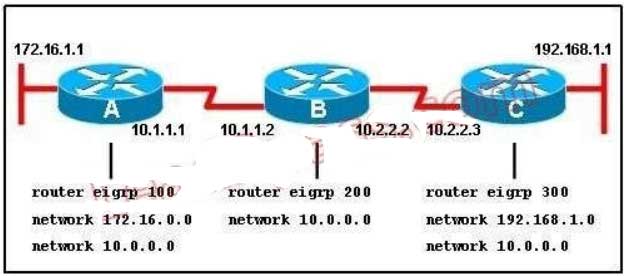
152. Refer to the exhibit. When running EIGRP, what is required for RouterA to exchange routing updates with RouterC?
A. AS numbers must be changed to match on all the routers
B. Loopback interfaces must be configured so a DR is elected
C. The no auto-summary command is needed on Router A and Router C
D. Router B needs to have two network statements, one for each connected network
Explanation/Reference:
This question is to examine the understanding of the interaction between EIGRP routers. The following information must be matched so as to create neighborhood. EIGRP routers to establish, must match the following information: 1. AS Number; 2. K value.
153. A router has two Fast Ethernet interfaces and needs to connect to four VLANs in the local network. How can you accomplish this task, using the fewest physical interfaces and without decreasing network performance?
A. Use a hub to connect the four VLANS with a Fast Ethernet interface on the router.
B. Add a second router to handle the VLAN traffic.
C. Add two more Fast Ethernet interfaces.
D. Implement a router-on-a-stick configuration.
Explanation/Reference:
A router on a stick allows you to use sub-interfaces to create multiple logical networks on a single physical interface.
154. Users on the 172.17.22.0 network cannot reach the server located on the 172.31.5.0 network. The network administrator connected to router Coffee via the console port, issued the show ip route command, and was able to ping the server .
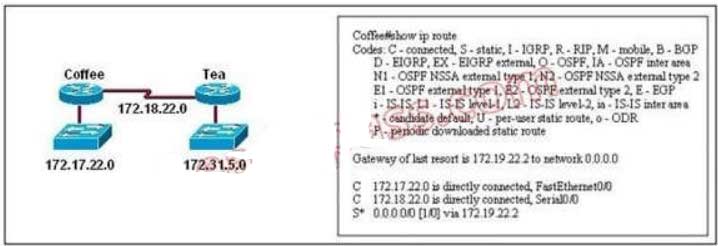
on the output of the show ip route command and the topology shown in the graphic, what is the cause of the failure?
A. The network has not fully converged.
B. IP routing is not enabled.
C. A static route is configured incorrectly
D. The FastEthernet interface on Coffee is disabled.
E. The neighbor relationship table is not correctly updated.
F. The routing table on Coffee has not updated .
Explanation/Reference:
The default route or the static route was configured with incorrect next-hop ip address 172.19.22.2 The correct ip address will be 172.18.22.2 to reach server located on 172.31.5.0 network. Ip route 0.0.0.0 0.0.0.0 172.18.22.2
155. A network administrator is trying to add a new router into an established OSPF network. The networks attached to the new router do not appear in the routing tables of the other OSPF routers. Given the information in the partial configuration shown below, what configuration error is causing this problem?
Router(config)# router ospf 1
Router(config-router)# network 10.0.0.0 255.0.0.0 area 0
A. The process id is configured improperly.
B. The OSPF area is configured improperly.
C. The network wildcard mask is configured improperly.
D. The network number is configured improperly.
E. The AS is configured improperly.
F. The network subnet mask is configured improperly.
Explanation/Reference:
When configuring OSPF, the mask used for the network statement is a wildcard mask similar to an access list. In this specific example, the correct syntax would have been “network 10.0.0.0 0.0.0.255 area 0.”
156. Which Cisco Catalyst feature automatically disables the port in an operational PortFast upon receipt of a BPDU?
A. BackboneFast B. UplinkFast
C. Root Guard
D. BPDU Guard
E. BPDU Filter
Explanation/Reference:
We only enable PortFast feature on access ports (ports connected to end stations). But if someone does not know he can accidentally plug that port to another switch and a loop may occur when BPDUs are being transmitted and received on these ports. With BPDU Guard, when a PortFast receives a BPDU, it will be shut down to prevent a loop.
157. When you are troubleshooting an ACL issue on a router, which command would you use to verify which interfaces are affected by the ACL?
A. show ip access-lists
B. show access-lists
C. show interface
D. show ip interface
E. list ip interface
Explanation/Reference:
Incorrect answer:
show ip access-lists does not show interfaces affected by an ACL.
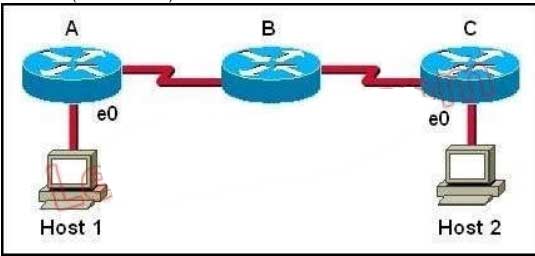
158. Host 1 is trying to communicate with Host 2. The e0 interface on Router C is down. Which of the following are true? (Choose two.)
A. Router C will use ICMP to inform Host 1 that Host 2 cannot be reached.
B. Router C will use ICMP to inform Router B that Host 2 cannot be reached.
C. Router C will use ICMP to inform Host 1, Router A, and Router B that Host 2 cannot be reached.
D. Router C will send a Destination Unreachable message type.
E. Router C will send a Router Selection message type.
F. Router C will send a Source Quench message type.
Explanation/Reference:
Host 1 is trying to communicate with Host 2. The e0 interface on Router C is down. Router C will send ICMP packets to inform Host 1 that Host 2 cannot be reached.
159. Refer to the exhibit. When running EIGRP, what is required for RouterA to exchange routing updates with RouterC?
A. AS numbers must be changed to match on all the routers
B. Loopback interfaces must be configured so a DR is elected
C. The no auto-summary command is needed on Router A and Router C
D. Router B needs to have two network statements, one for each connected network
Explanation/Reference:
This question is to examine the understanding of the interaction between EIGRP routers. The following information must be matched so as to create neighborhood. EIGRP routers to establish, must match the following information: 1. AS Number; 2. K value.
160. Cisco Catalyst switches CAT1 and CAT2 have a connection between them using ports FA0/13. An 802.1Q trunk is configured between the two switches. On CAT1, VLAN 10 is chosen as native, but on CAT2 the native VLAN is not specified. What will happen in this scenario?
A. 802.1Q giants frames could saturate the link.
B. VLAN 10 on CAT1 and VLAN 1 on CAT2 will send untagged frames.
C. A native VLAN mismatch error message will appear.
D. VLAN 10 on CAT1 and VLAN 1 on CAT2 will send tagged frames.
Explanation/Reference:
A “native VLAN mismatch” error will appear by CDP if there is a native VLAN mismatch on an 802.1Q link. “VLAN mismatch” can cause traffic from one vlan to leak into another vlan.
161. Refer to the exhibit. A network technician is asked to design a small network with redundancy. The exhibit represents this design, with all hosts configured in the same VLAN. What conclusions can be made about this design?
A. This design will function as intended.
B. Spanning-tree will need to be used.
C. The router will not accept the addressing scheme.
D. The connection between switches should be a trunk.
E. The router interfaces must be encapsulated with the 802.1Q protocol.
Explanation/Reference:
Each interface on a router must be in a different network. If two interfaces are in the same network, the router will not accept it and show error when the administrator assigns it.
162. Refer to the exhibit. A technician is troubleshooting host connectivity issues on the switches. The hosts in VLANs 10 and 15 on Sw11 are unable to communicate with hosts in the same VLANs on Sw12. Hosts in the Admin VLAN are able to communicate. The port-to-VLAN assignments are identical on the two switches. What could be the problem?
A. The Fa0/1 port is not operational on one of the switches.
B. The link connecting the switches has not been configured as a trunk.
C. At least one port needs to be configured in VLAN 1 for VLANs 10 and 15 to be able to communicate.
D. Port FastEthernet 0/1 needs to be configured as an access link on both switches.
E. A router is required for hosts on SW11 in VLANs 10 and 15 to communicate with hosts in the same
VLAN on Sw12.
Explanation/Reference:
In order for hosts in the same VLAN to communicate with each other over multiple switches, those switches need to be configured as trunks on their connected interfaces so that they can pass traffic from multiple VLANs.
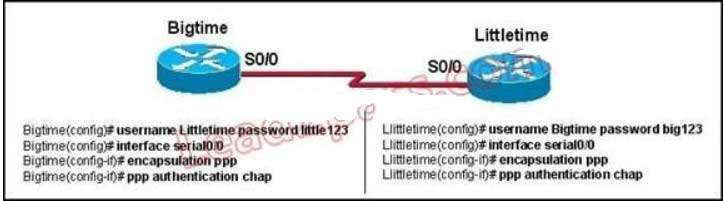
163. Refer to the exhibit. The Bigtime router is unable to authenticate to the Littletime router. What is the cause of the problem?
A. The usernames are incorrectly configured on the two routers.
B. The passwords do not match on the two routers.
C. CHAP authentication cannot be used on a serial interface. D. The routers cannot be connected from interface S0/0 to interface S0/0.
E. With CHAP authentication, one router must authenticate to another router. The routers cannot be configured to authenticate to each other.
Explanation/Reference:
With CHAP authentication, the configured passwords must be identical on each router. Here, it is configured as little123 on one side and big123 on the other.
164. Refer to the exhibit. Given this output for SwitchC, what should the network administrator’s next action be?
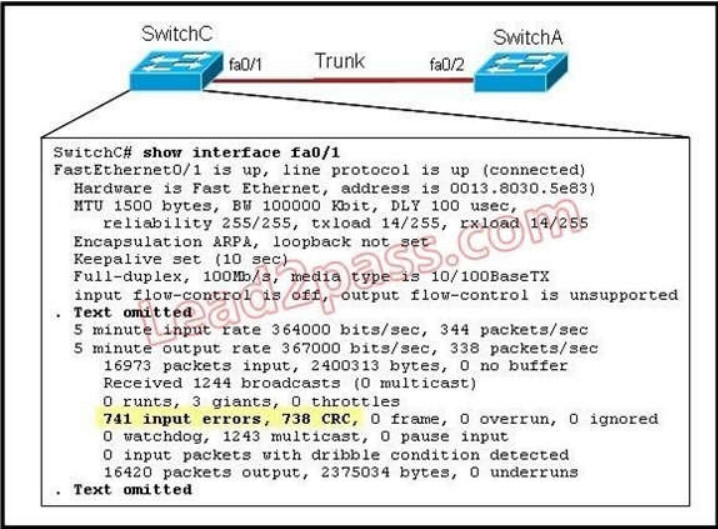
A. Check the trunk encapsulation mode for SwitchC’s fa0/1 port.
B. Check the duplex mode for SwitchC’s fa0/1 port.
C. Check the duplex mode for SwitchA’s fa0/2 port.
D. Check the trunk encapsulation mode for SwitchA’s fa0/2 port.
Explanation/Reference:
Here we can see that this port is configured for full duplex, so the next step would be to check the duplex setting of the port on the other switch. A mismatched trunk encapsulation would not result in input errors and CRC errors.
165. What will happen if a private IP address is assigned to a public interface connected to an ISP?
A. Addresses in a private range will be not be routed on the Internet backbone.
B. Only the ISP router will have the capability to access the public network.
C. The NAT process will be used to translate this address to a valid IP address.
D. A conflict of IP addresses happens, because other public routers can use the same range.
Explanation/Reference:
Private RFC 1918 IP addresses are meant to be used by organizations locally within their own network only, and can not be used globally for Internet use.
166. Refer to the exhibit. An attempt to deny web access to a subnet blocks all traffic from the subnet. Which interface command immediately removes the effect of ACL 102?
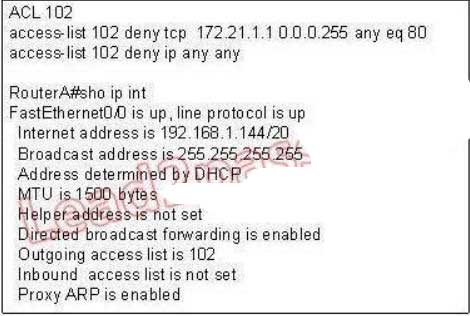
A. no ip access-class 102 in
B. no ip access-class 102 out
C. no ip access-group 102 in
D. no ip access-group 102 out
E. no ip access-list 102 in
Explanation/Reference:
Now let’s find out the range of the networks on serial link:
For the network 192.168.1.62/27:
Increment: 32
Network address: 192.168.1.32
Broadcast address: 192.168.1.63 For the network 192.168.1.65/27:
Increment: 32
Network address: 192.168.1.64
Broadcast address: 192.168.1.95
-> These two IP addresses don’t belong to the same network and they can’t see each other
167. Which router IOS commands can be used to troubleshoot LAN connectivity problems? (Choose three.)
A. ping
B. tracert C. ipconfig
D. show ip route
E. winipcfg
F. show interfaces
Explanation/Reference:
Ping, show ip route, and show interfaces are all valid troubleshooting IOS commands. Tracert, ipconfig, and winipcfg are PC commands, not IOS.
168. A network administrator is troubleshooting the OSPF configuration of routers R1 and R2. The routers cannot establish an adjacency relationship on their common Ethernet link.
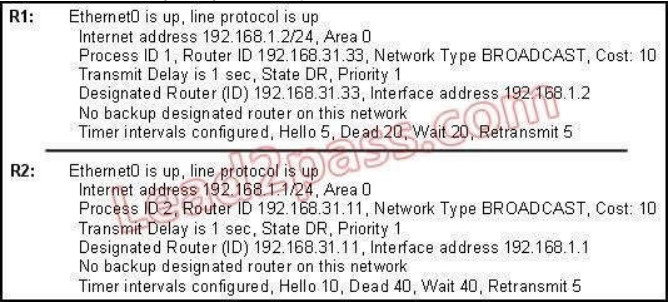
The graphic shows the output of the show ip ospf interface e0 command for routers R1 and R2. Based on the information in the graphic, what is the cause of this problem?
A. The OSPF area is not configured properly.
B. The priority on R1 should be set higher.
C. The cost on R1 should be set higher.
D. The hello and dead timers are not configured properly.
E. A backup designated router needs to be added to the network.
F. The OSPF process ID numbers must match.
Explanation/Reference:
In OSPF, the hello and dead intervals must match and here we can see the hello interval is set to 5 on R1 and 10 on R2. The dead interval is also set to 20 on R1 but it is 40 on R2.
169. In which circumstance are multiple copies of the same unicast frame likely to be transmitted in a switched LAN?
A. during high traffic periods
B. after broken links are re-established
C. when upper-layer protocols require high reliability
D. in an improperly implemented redundant topology
E. when a dual ring topology is in use
Explanation/Reference:
If we connect two switches via 2 or more links and do not enable STP on these switches then a loop (which creates multiple copies of the same unicast frame) will occur. It is an example of an improperly implemented redundant topology.
170. VLAN 3 is not yet configured on your switch. What happens if you set the switchport access vlan 3
command in interface configuration mode?
A. The command is rejected.
B. The port turns amber.
C. The command is accepted and the respective VLAN is added to vlan.dat.
D. The command is accepted and you must configure the VLAN manually.
Explanation/Reference:
The “switchport access vlan 3” will put that interface as belonging to VLAN 3 while also updated the VLAN database automatically to include VLAN 3.
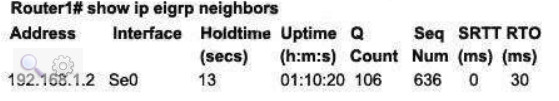
171. A network administrator is troubleshooting an EIGRP problem on a router and needs to confirm the IP addresses of the devices with which the router has established adjacency. The retransmit interval and the queue counts for the adjacent routers also need to be checked. What command will display the required information?
A. Router# show ip eigrp adjacency
B. Router# show ip eigrp topology
C. Router# show ip eigrp interfaces
D. Router# show ip eigrp neighbors
Explanation/Reference:
Below is an example of the show ip eigrp neighbors command. The retransmit interval (Smooth Round Trip Timer – SRTT) and the queue counts (Q count, which shows the number of queued EIGRP packets) for the adjacent routers are listed:
172. Refer to the graphic. R1 is unable to establish an OSPF neighbor relationship with R3. What are possible reasons for this problem? (Choose two.)
A. All of the routers need to be configured for backbone Area 1.
B. R1 and R2 are the DR and BDR, so OSPF will not establish neighbor adjacency with R3.
C. A static route has been configured from R1 to R3 and prevents the neighbor adjacency from being
established.
D. The hello and dead interval timers are not set to the same values on R1 and R3.
E. EIGRP is also configured on these routers with a lower administrative distance.
F. R1 and R3 are configured in different areas.
Explanation/Reference:
This question is to examine the conditions for OSPF to create neighborhood. So as to make the two routers become neighbors, each router must be matched with the following items: The area ID and its types; Hello and failure time interval timer; OSPF Password (Optional);
173. Refer to the exhibit. The network shown in the diagram is experiencing connectivity problems. Which of the following will correct the problems? (Choose two.)
A. Configure the gateway on Host A as 10.1.1.1.
B. Configure the gateway on Host B as 10.1.2.254.
C. Configure the IP address of Host A as 10.1.2.2.
D. Configure the IP address of Host B as 10.1.2.2.
E. Configure the masks on both hosts to be 255.255.255.224.
F. Configure the masks on both hosts to be 255.255.255.240.
Explanation/Reference:
The switch 1 is configured with two VLANs: VLAN1 and VLAN2. The IP information of member Host A in
VLAN1 is as follows:
Address : 10.1.1.126
Mask : 255.255.255.0
Gateway : 10.1.1.254
The IP information of member Host B in VLAN2 is as follows:
Address : 10.1.1.12
Mask : 255.255.255.0
Gateway : 10.1.1.254
The configuration of sub-interface on router 2 is as follows:
Fa0/0.1 — 10.1.1.254/24 VLAN1
Fa0/0.2 — 10.1.2.254/24 VLAN2
It is obvious that the configurations of the gateways of members in VLAN2 and the associated network segments are wrong. The layer3 addressing information of Host B should be modified as follows:
Address : 10.1.2.X
Mask : 255.255.255.0
174. Refer to the exhibit. A problem with network connectivity has been observed. It is suspected that the cable connected to switch port Fa0/9 on Switch1 is disconnected. What would be an effect of this cable being disconnected?
A. Host B would not be able to access the server in VLAN9 until the cable is reconnected.
B. Communication between VLAN3 and the other VLANs would be disabled.
C. The transfer of files from Host B to the server in VLAN9 would be significantly slower.
D. For less than a minute, Host B would not be able to access the server in VLAN9. Then normal network function would resume.
Explanation/Reference:
Spanning-Tree Protocol (STP) is a Layer 2 protocol that utilizes a special-purpose algorithm to discover physical loops in a network and effect a logical loop-free topology. STP creates a loop- free tree structure consisting of leaves and branches that span the entire Layer 2 network. The actual mechanics of how bridges communicate and how the STP algorithm works will be discussed at length in the following topics. Note that the terms bridge and switch are used interchangeably when discussing STP. In addition, unless otherwise indicated, connections between switches are assumed to be trunks.
175. Refer to the exhibit. HostA cannot ping HostB. Assuming routing is properly configured, what is the cause of this problem?
A. HostA is not on the same subnet as its default gateway.
B. The address of SwitchA is a subnet address.
C. The Fa0/0 interface on RouterA is on a subnet that can’t be used.
D. The serial interfaces of the routers are not on the same subnet.
E. The Fa0/0 interface on RouterB is using a broadcast address.
Explanation/Reference:
Now let’s find out the range of the networks on serial link:
For the network 192.168.1.62/27:
Increment: 32
Network address: 192.168.1.32
Broadcast address: 192.168.1.63 For the network 192.168.1.65/27:
Increment: 32
Network address: 192.168.1.64
Broadcast address: 192.168.1.95
-> These two IP addresses don’t belong to the same network and they can’t see each other
176. Which port state is introduced by Rapid-PVST?
A. learning
B. listening
C. discarding
D. forwarding
Explanation/Reference:
PVST+ is based on IEEE802.1D Spanning Tree Protocol (STP). But PVST+ has only 3 port states (discarding, learning and forwarding) while STP has 5 port states (blocking, listening, learning, forwardingand disabled). So discarding is a new port state in PVST+.
177. Refer to the exhibit. The two connected ports on the switch are not turning orange or green. What would be the most effective steps to troubleshoot this physical layer problem? (Choose three.)
A. Ensure that the Ethernet encapsulations match on the interconnected router and switch ports.
B. Ensure that cables A and B are straight-through cables.
C. Ensure cable A is plugged into a trunk port.
D. Ensure the switch has power.
E. Reboot all of the devices.
F. Reseat all cables.
Explanation/Reference:
The ports on the switch are not up indicating it is a layer 1 (physical) problem so we should check cable type, power and how they are plugged in.
178. Refer to the exhibit. A network administrator attempts to ping Host2 from Host1 and receives the results that are shown. What is the problem?
A. The link between Host1 and Switch1 is down.
B. TCP/IP is not functioning on Host1
C. The link between Router1 and Router2 is down.
D. The default gateway on Host1 is incorrect.
E. Interface Fa0/0 on Router1 is shutdown.
F. The link between Switch1 and Router1 is down
Explanation/Reference:
Host1 tries to communicate with Host2. The message destination host unreachable from Router1 indicates that the problem occurs when the data is forwarded from Host1 to Host2. According to the topology, we can infer that The link between Router1 and Router2 is down.
179. Refer to the exhibit. Hosts in network 192.168.2.0 are unable to reach hosts in network 192.168.3.0. Based on the output from RouterA, what are two possible reasons for the failure? (Choose two.)
A. The cable that is connected to S0/0 on RouterA is faulty.
B. Interface S0/0 on RouterB is administratively down.
C. Interface S0/0 on RouterA is configured with an incorrect subnet mask.
D. The IP address that is configured on S0/0 of RouterB is not in the correct subnet
E. Interface S0/0 on RouterA is not receiving a clock signal from the CSU/DSU.
F. The encapsulation that is configured on S0/0 of RouterB does not match the encapsulation that is configured on S0/0 of RouterA
Explanation/Reference:
From the output we can see that there is a problem with the Serial 0/0 interface. It is enabled, but the line protocol is down. The could be a result of mismatched encapsulation or the interface not receiving a clock signal from the CSU/DSU.
180. Refer to the exhibit. An administrator pings the default gateway at 10.10.10.1 and sees the output as
shown. At which OSI layer is the problem?
A. data link layer
B. application layer
C. access layer
D. session layer
E. network layer
Explanation/Reference:
The command ping uses ICMP protocol, which is a network layer protocol used to propagate control message between host and router. The command ping is often used to verify the network connectivity, so it works at the network layer.
181. Which statement is correct regarding the operation of DHCP?
A. A DHCP client uses a ping to detect address conflicts.
B. A DHCP server uses a gratuitous ARP to detect DHCP clients.
C. A DHCP client uses a gratuitous ARP to detect a DHCP server.
D. If an address conflict is detected, the address is removed from the pool and an administrator must resolve the conflict.
E. If an address conflict is detected, the address is removed from the pool for an amount of time
configurable by the administrator.
F. If an address conflict is detected, the address is removed from the pool and will not be reused until the server is rebooted.
Explanation/Reference:
An address conflict occurs when two hosts use the same IP address. During address assignment, DHCP checks for conflicts using ping and gratuitous ARP. If a conflict is detected, the address is removed from the pool. The address will not be assigned until the administrator resolves the conflict.
182. Refer to the exhibit. Statements A, B, C, and D of ACL 10 have been entered in the shown order and applied to interface E0 inbound, to prevent all hosts (except those whose addresses are the first and last IP of subnet 172.21.1.128/28) from accessing the network. But as is, the ACL does not restrict anyone from the network. How can the ACL statements be re-arranged so that the system works as intended?
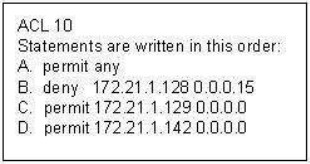
A. ACDB
B. BADC
C. DBAC
D. CDBA
Explanation/Reference:
Routers go line by line through an access list until a match is found and then will not look any further, even if a more specific of better match is found later on in the access list. So, it it best to begin with the most specific entries first, in this cast the two hosts in line C and D. Then, include the subnet (B) and then finally the rest of the traffic (A)
183. The output of the show frame-relay pvc command shows “PVC STATUS = INACTIVE”. What does this mean?
A. The PVC is configured correctly and is operating normally, but no data packets have been detected for
more than five minutes.
B. The PVC is configured correctly, is operating normally, and is no longer actively seeking the address of
the remote router.
C. The PVC is configured correctly, is operating normally, and is waiting for interesting traffic to trigger a
call to the remote router.
D. The PVC is configured correctly on the local switch, but there is a problem on the remote end of the PVC.
E. The PVC is not configured on the local switch.
Explanation/Reference:
The PVC STATUS displays the status of the PVC. The DCE device creates and sends the report to the
DTE devices. There are 4 statuses:
+ ACTIVE: the PVC is operational and can transmit data + INACTIVE: the connection from the local router to the switch is working, but the connection to the remote router is not available + DELETED: the PVC is not present and no LMI information is being received from the Frame Relay switch
+ STATIC: the Local Management Interface (LMI) mechanism on the interface is disabled (by using the “nokeepalive” command). This status is rarely seen so it is ignored in some books.
184. Which command is used to enable CHAP authentication, with PAP as the fallback method, on a serial
interface?
A. Router(config-if)# ppp authentication chap fallback ppp
B. Router(config-if)# ppp authentication chap pap
C. Router(config-if)# authentication ppp chap fallback ppp
D. Router(config-if)# authentication ppp chap pap
Explanation/Reference:
This command tells the router to first use CHAP and then go to PAP if CHAP isn’t available
185. Which protocol is an open standard protocol framework that is commonly used in VPNs, to provide secure
end-to-end communications?
A. RSA
B. L2TP
C. IPsec
D. PPTP
Explanation/Reference:
IPSec is a framework of open standards that provides data confidentiality, data integrity, and data authentication between participating peers at the IP layer. IPSec can be used to protect one or more data flows between IPSec peers.
186. At which layer of the OSI model does PPP perform?
A. Layer 2
B. Layer 3
C. Layer 4
D. Layer 5
Explanation/Reference:
The Point-to-Point Protocol (PPP) provides a standard method for transporting multi-protocol datagrams over point-to-point links. PPP was originally emerged as an encapsulation protocol for transporting IP traffic between two peers. It is a data link layer protocol (layer 2 in the OSI model
187. The command frame-relay map ip 10.121.16.8 102 broadcast was entered on the router. Which of the following statements is true concerning this command?
A. This command should be executed from the global configuration mode.
B. The IP address 10.121.16.8 is the local router port used to forward data. C. 102 is the remote DLCI that will receive the information
D. This command is required for all Frame Relay configurations.
E. The broadcast option allows packets, such as RIP updates, to be forwarded across the PVC.
Explanation/Reference:
Broadcast is added to the configurations of the frame relay, so the PVC supports broadcast, allowing the routing protocol updates that use the broadcast update mechanism to be forwarded across itself.
188. Which two options are valid WAN connectivity methods? (Choose two.)
A. PPP
B. WAP
C. DSL
D. L2TPv3
E. Ethernet
Explanation/Reference:
The Point-to-Point Protocol (PPP) provides a standard method for transporting multi-protocol datagrams over point-to-point links. PPP was originally emerged as an encapsulation protocol for transporting IP traffic
between two peers. It is a data link layer protocol used for WAN connections. DSL is also considered a WAN connection, as it can be used to connect networks, typically when used with VPN technology.
189. Which Layer 2 protocol encapsulation type supports synchronous and asynchronous circuits and has built-in security mechanisms?
A. HDLC
B. PPP
C. X.25
D. Frame Relay
Explanation/Reference:
PPP: Provides router-to-router and host-to-network connections over synchronous and asynchronous circuits. PPP was designed to work with several network layer protocols, including IP. PPP also has built-in security mechanisms, such as Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP).
190. Which encapsulation type is a Frame Relay encapsulation type that is supported by Cisco routers?
A. IETF
B. ANSI Annex D
C. Q9333-A Annex A
D. HDLC
Explanation/Reference:
Cisco supports two Frame Relay encapsulation types: the Cisco encapsulation and the IETF Frame Relay encapsulation, which is in conformance with RFC 1490 and RFC 2427. The former is often used to connect two Cisco routers while the latter is used to connect a Cisco router to a non-Cisco router. You can test with your Cisco router when typing the command Router(configif)# encapsulation frame-relay ? on a WAN link. Below is the output of this command (notice Cisco is the default encapsulation so it is not listed here, just press Enter to use it).
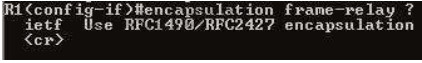
Note: Three LMI options are supported by Cisco routers are ansi, Cisco, and Q933a. They represent the ANSI Annex D, Cisco, and ITU Q933-A (Annex A) LMI types, respectively. HDLC is a WAN protocol same as Frame-Relay and PPP so it is not a Frame Relay encapsulation type
191. RouterA is unable to reach RouterB. Both routers are running IOS version 12.0. After reviewing the
command output and graphic, what is the most likely cause of the problem?
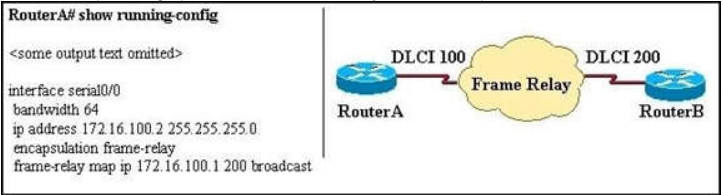
A. incorrect bandwidth configuration
B. incorrect LMI configuration
C. incorrect map statement
D. incorrect IP address
Explanation/Reference:
First we have to say this is an unclear question and it is wrong. The “frame-relay map ip” statement is correct thus none of the four answers above is correct. But we guess there is a typo in the output. Maybe the “ip address 172.16.100.2 255.255.0.0 command should be “ip address 172.16.100.1 255.255.0.0.
192. Refer to the exhibit. What is the meaning of the term dynamic as displayed in the output of the show frame-relay map command shown?
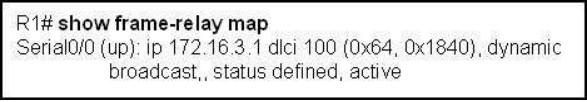
A. The Serial0/0 interface is passing traffic.
B. The DLCI 100 was dynamically allocated by the router.
C. The Serial0/0 interface acquired the IP address of 172.16.3.1 from a DHCP server. D. The DLCI 100 will be dynamically changed as required to adapt to changes in the Frame Relay cloud.
E. The mapping between DLCI 100 and the end station IP address 172.16.3.1 was learned through Inverse ARP.
Explanation/Reference:
Inverse Address Resolution Protocol (Inverse ARP) was developed to provide a mechanism for dynamic DLCI to Layer 3 address maps. Inverse ARP works much the same way Address Resolution Protocol (ARP) works on a LAN. However, with ARP, the device knows the Layer 3 IP address and needs to know the remote data link MAC address. With Inverse ARP, the router knows the Layer 2 address which is the DLCI, but needs to know the remote Layer 3 IP address. When using dynamic address mapping, Inverse ARP requests a next-hop protocol address for each active PVC. Once the requesting router receives an Inverse ARP response, it updates its DLCI-to-Layer 3 address mapping table. Dynamic address mapping is enabled by default for all protocols enabled on a physical interface. If the Frame Relay environment supports LMI autosensing and Inverse ARP, dynamic address mapping takes place automatically. Therefore, no static address mapping is required.
193. A network administrator needs to configure a serial link between the main office and a remote location. The router at the remote office is a non-Cisco router. How should the network administrator configure the serial interface of the main office router to make the connection
A. Main(config)# interface serial 0/0
Main(config-if)# ip address 172.16.1.1 255.255.255.252 Main(config-if)# no shut
B. Main(config)# interface serial 0/0
Main(config-if)# ip address 172.16.1.1 255.255.255.252
Main(config-if)# encapsulation ppp Main(config-if)# no shut
C. Main(config)# interface serial 0/0
Main(config-if)# ip address 172.16.1.1 255.255.255.252
Main(config-if)# encapsulation frame-relay
Main(config-if)# authentication chap
Main(config-if)# no shut
D. Main(config)# interface serial 0/0
Main(config-if)#ip address 172.16.1.1 255.255.255.252
Main(config-if)#encapsulation ietf
Main(config-if)# no shut
Explanation/Reference:
With serial point to point links there are two options for the encapsulation. The default, HDLC, is Cisco proprietary and works only with other Cisco routers. The other option is PPP which is standards based and
supported by all vendors.
194. What are three reasons that an organization with multiple branch offices and roaming users might
implement a Cisco VPN solution instead of point-to-point WAN links? (Choose three.)
A. reduced cost
B. better throughput
C. broadband incompatibility
D. increased security
E. scalability
F. reduced latency
Explanation/Reference:
IPsec offer a number of advantages over point to point WAN links, particularly when multiple locations are involved. These include reduced cost, increased security since all traffic is encrypted, and increased scalability as s single WAN link can be used to connect to all locations in a VPN, where as a point to point link would need to be provisioned to each location.
195. Which two statistics appear in show frame-relay map output? (Choose two.)
A. the number of BECN packets that are received by the router
B. the value of the local DLCI
C. the number of FECN packets that are received by the router
D. the status of the PVC that is configured on the router
E. the IP address of the local router
Explanation/Reference:
Sample “show frame-relay map” output:
R1#sh frame mapSerial0/0 (up): ip 10.4.4.1 dlci 401(0x191,0x6410), dynamic,broadcast,, status defined,
activeSerial0/0 (up): ip 10.4.4.3 dlci 403(0x193,0x6430), dynamic,broadcast,, status defined, activeSerial0/0
(up): ip 10.4.4.4 dlci 401(0x191,0x6410), static,CISCO, status defined, active
196. Users have been complaining that their Frame Relay connection to the corporate site is very slow. The network administrator suspects that the link is overloaded.
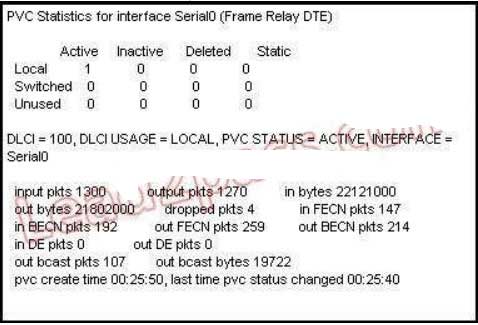
Based on the partial output of the Router# show frame relay pvc command shown in the graphic, which
output value indicates to the local router that traffic sent to the corporate site is experiencing congestion?
A. DLCI = 100
B. last time PVC status changed 00:25:40
C. in BECN packets 192
D. in FECN packets 147
E. in DE packets 0
Explanation/Reference:
If device A is sending data to device B across a Frame Relay infrastructure and one of the intermediate
Frame Relay switches encounters congestion, congestion being full buffers, over- subscribed port, overloaded resources, etc, it will set the BECN bit on packets being returned to the sending device and the FECN bit on the packets being sent to the receiving device.
197. Which command allows you to verify the encapsulation type (CISCO or IETF) for a Frame Relay link?
A. show frame-relay lmi
B. show frame-relay map
C. show frame-relay pvc
D. show interfaces serial
Explanation/Reference:
When connecting Cisco devices with non-Cisco devices, you must use IETF4 encapsulation on both devices. Check the encapsulation type on the Cisco device with the show frame-relay map exec command.
198. It has become necessary to configure an existing serial interface to accept a second Frame Relay virtual circuit. Which of the following procedures are required to accomplish this task? (Choose three.)
A. Remove the IP address from the physical interface.
B. Encapsulate the physical interface with multipoint PPP.
C. Create the virtual interfaces with the interface command
D. Configure each subinterface with its own IP address.
E. Disable split horizon to prevent routing loops between the subinterface networks.
F. Configure static Frame Relay map entries for each subinterface network.
Explanation/Reference:
For multiple PVC’s on a single interface, you must use subinterfaces, with each subinterface configured for each PVC. Each subinterface will then have its own IP address, and no IP address will be assigned to the main interface.
199.What occurs on a Frame Relay network when the CIR is exceeded?
A. All TCP traffic is marked discard eligible.
B. All UDP traffic is marked discard eligible and a BECN is sent.
C. All TCP traffic is marked discard eligible and a BECN is sent.
D. All traffic exceeding the CIR is marked discard eligible.
Explanation/Reference:
Committed information rate (CIR): The minimum guaranteed data transfer rate agreed to by the Frame Relay switch. Frames that are sent in excess of the CIR are marked as discard eligible (DE) which means they can be dropped if the congestion occurs within the Frame Relay network. Note: In the Frame Relayframe format, there is a bit called Discard eligible (DE) bit that is used to identify frames that are first to be dropped when the CIR is exceeded.
200. Which two statements about using the CHAP authentication mechanism in a PPP link are true? (Choose two.)
A. CHAP uses a two-way handshake.
B. CHAP uses a three-way handshake.
C. CHAP authentication periodically occurs after link establishment.
D. CHAP authentication passwords are sent in plaintext.
E. CHAP authentication is performed only upon link establishment.
F. CHAP has no protection from playback attacks.
Explanation/Reference:
CHAP is an authentication scheme used by Point to Point Protocol (PPP) servers to validate the identity of remote clients. CHAP periodically verifies the identity of the client by using a three-way handshake. This happens at the time of establishing the initial link (LCP), and may happen again at any time afterwards. The verification is based on a shared secret (such as the client user’s password).
201. Refer to the exhibit. Which statement describes DLCI 17?
A. DLCI 17 describes the ISDN circuit between R2 and R3.
B. DLCI 17 describes a PVC on R2. It cannot be used on R3 or R1.
C. DLCI 17 is the Layer 2 address used by R2 to describe a PVC to R3.
D. DLCI 17 describes the dial-up circuit from R2 and R3 to the service provider.
Explanation/Reference:
DLCI-Data Link Connection Identifier Bits: The DLCI serves to identify the virtual connection so that the receiving end knows which information connection a frame belongs to. Note that this DLCI has only local significance. Frame Relay is strictly a Layer 2 protocol suite.