[box type=”success” align=”” class=”” width=””]How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer.[/box][box type=”warning” align=”” class=”” width=””]NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.[/box]
- What is a result of connecting two or more switches together?
- The number of broadcast domains is increased.
- The size of the broadcast domain is increased.*
- The number of collision domains is reduced.
- The size of the collision domain is increased.
[box type=”info” align=”alignleft” class=”” width=””]Explain:
When two or more switches are connected together, the size of the broadcast domain is increased and so is the number of collision domains. The number of broadcast domains is increased only when routers are added.
[/box] - Refer to the exhibit. How many broadcast domains are there?
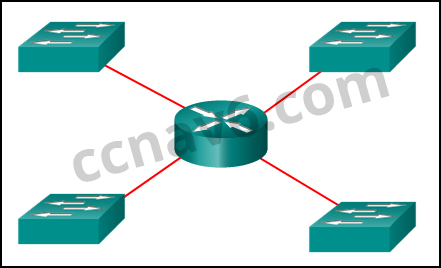
- 1
- 2
- 3
- 4*
[box type=”info” align=”alignleft” class=”” width=””]Explain:
A router is used to route traffic between different networks. Broadcast traffic is not permitted to cross the router and therefore will be contained within the respective subnets where it originated.
[/box] - What are two reasons a network administrator might want to create subnets? (Choose two.)
- simplifies network design
- improves network performance *
- easier to implement security policies*
- reduction in number of routers needed
- reduction in number of switches needed
[box type=”info” align=”alignleft” class=”” width=””]Explain:
Two reasons for creating subnets include reduction of overall network traffic and improvement of network performance. Subnets also allow an administrator to implement subnet-based security policies. The number of routers or switches is not affected. Subnets do not simplify network design.
[/box] - Refer to the exhibit. A company uses the address block of 128.107.0.0/16 for its network. What subnet mask would provide the maximum number of equal size subnets while providing enough host addresses for each subnet in the exhibit?
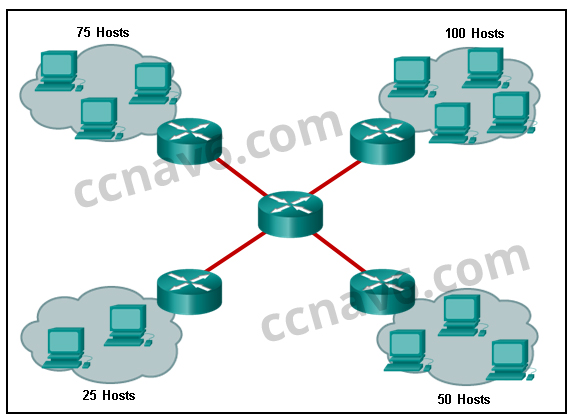
- 255.255.255.0
- 255.255.255.128*
- 255.255.255.192
- 255.255.255.224
- 255.255.255.240
[box type=”info” align=”alignleft” class=”” width=””]Explain:
The largest subnet in the topology has 100 hosts in it so the subnet mask must have at least 7 host bits in it (27-2=126). 255.255.255.0 has 8 hosts bits, but this does not meet the requirement of providing the maximum number of subnets.
[/box] - Refer to the exhibit. The network administrator has assigned the LAN of LBMISS an address range of 192.168.10.0. This address range has been subnetted using a /29 prefix. In order to accommodate a new building, the technician has decided to use the fifth subnet for configuring the new network (subnet zero is the first subnet). By company policies, the router interface is always assigned the first usable host address and the workgroup server is given the last usable host address. Which configuration should be entered into the properties of the workgroup server to allow connectivity to the Internet?
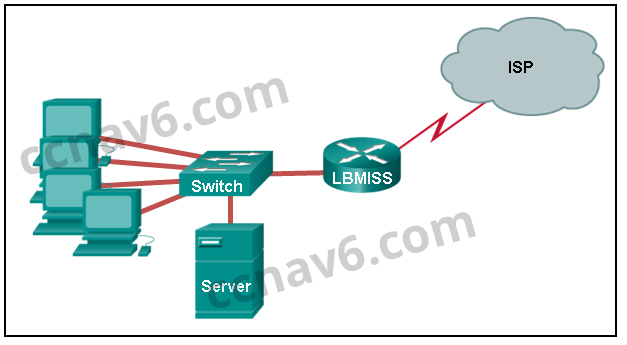
- IP address: 192.168.10.65 subnet mask: 255.255.255.240, default gateway: 192.168.10.76
- IP address: 192.168.10.38 subnet mask: 255.255.255.240, default gateway: 192.168.10.33
- IP address: 192.168.10.38 subnet mask: 255.255.255.248, default gateway: 192.168.10.33*
- IP address: 192.168.10.41 subnet mask: 255.255.255.248, default gateway: 192.168.10.46
- IP address: 192.168.10.254 subnet mask: 255.255.255.0, default gateway: 192.168.10.1
[box type=”info” align=”alignleft” class=”” width=””]Explain:
Using a /29 prefix to subnet 192.168.10.0 results in subnets that increment by 8:
192.168.10.0 (1)
192.168.10.8 (2)
192.168.10.16 (3)
192.168.10.24 (4)
192.168.10.32 (5)
[/box] - If a network device has a mask of /28, how many IP addresses are available for hosts on this network?
- 256
- 254
- 62
- 32
- 16
- 14*
[box type=”info” align=”alignleft” class=”” width=””]Explain:
A /28 mask is the same as 255.255.255.240. This leaves 4 host bits. With 4 host bits, 16 IP addresses are possible, but one address represents the subnet number and one address represents the broadcast address. 14 addresses can then be used to assign to network devices.
[/box] - Which subnet mask would be used if 5 host bits are available?
- 255.255.255.0
- 255.255.255.128
- 255.255.255.224*
- 255.255.255.240
[box type=”info” align=”alignleft” class=”” width=””]Explain:
The subnet mask of 255.255.255.0 has 8 host bits. The mask of 255.255.255.128 results in 7 host bits. The mask of 255.255.255.224 has 5 host bits. Finally, 255.255.255.240 represents 4 host bits.
[/box] - How many host addresses are available on the network 172.16.128.0 with a subnet mask of 255.255.252.0?
- 510
- 512
- 1022*
- 1024
- 2046
- 2048
[box type=”info” align=”alignleft” class=”” width=””]Explain:
A mask of 255.255.252.0 is equal to a prefix of /22. A /22 prefix provides 22 bits for the network portion and leaves 10 bits for the host portion. The 10 bits in the host portion will provide 1022 usable IP addresses (2^10 – 2 = 1022).
[/box] - How many bits must be borrowed from the host portion of an address to accommodate a router with five connected networks?
- two
- three*
- four
- five
[box type=”info” align=”alignleft” class=”” width=””]Explain:
Each network that is directly connected to an interface on a router requires its own subnet. The formula 2n, where n is the number of bits borrowed, is used to calculate the available number of subnets when borrowing a specific number of bits.
[/box] - A network administrator wants to have the same network mask for all networks at a particular small site. The site has the following networks and number of devices:
IP phones – 22 addresses
PCs – 20 addresses needed
Printers – 2 addresses needed
Scanners – 2 addresses needed
The network administrator has deemed that 192.168.10.0/24 is to be the network used at this site. Which single subnet mask would make the most efficient use of the available addresses to use for the four subnetworks?- 255.255.255.0
- 255.255.255.192
- 255.255.255.224*
- 255.255.255.240
- 255.255.255.248
- 255.255.255.252
[box type=”info” align=”alignleft” class=”” width=””]Explain:
If the same mask is to be used, then the network with the most hosts must be examined for the number of hosts, which in this case is 22 hosts. Thus, 5 host bits are needed. The /27 or 255.255.255.224 subnet mask would be appropriate to use for these networks.
[/box] - A company has a network address of 192.168.1.64 with a subnet mask of 255.255.255.192. The company wants to create two subnetworks that would contain 10 hosts and 18 hosts respectively. Which two networks would achieve that? (Choose two.)
- 192.168.1.16/28
- 192.168.1.64/27*
- 192.168.1.128/27
- 192.168.1.96/28*
- 192.168.1.192/28
[box type=”info” align=”alignleft” class=”” width=””]Explain:
Subnet 192.168.1.64 /27 has 5 bits that are allocated for host addresses and therefore will be able to support 32 addresses, but only 30 valid host IP addresses. Subnet 192.168.1.96/28 has 4 bits for host addresses and will be able to support 16 addresses, but only 14 valid host IP addresses
[/box] - A network administrator is variably subnetting a network. The smallest subnet has a mask of 255.255.255.248. How many usable host addresses will this subnet provide?
- 4
- 6*
- 8
- 10
- 12
[box type=”info” align=”alignleft” class=”” width=””]Explain:
The mask 255.255.255.248 is equivalent to the /29 prefix. This leaves 3 bits for hosts, providing a total of 6 usable IP addresses (23 = 8 – 2 = 6).
[/box] - Refer to the exhibit. Given the network address of 192.168.5.0 and a subnet mask of 255.255.255.224, how many total host addresses are unused in the assigned subnets?
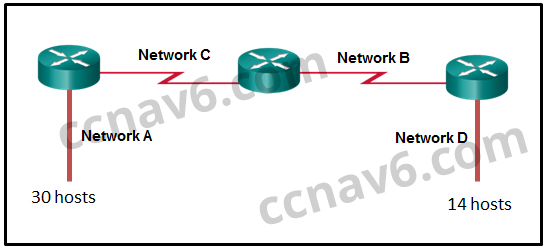
- 56
- 60
- 64
- 68
- 72*
[box type=”info” align=”alignleft” class=”” width=””]Explain:
The network IP address 192.168.5.0 with a subnet mask of 255.255.255.224 provides 30 usable IP addresses for each subnet. Subnet A needs 30 host addresses. There are no addresses wasted. Subnet B uses 2 of the 30 available IP addresses, because it is a serial link. Consequently, it wastes 28 addresses. Likewise, subnet C wastes 28 addresses. Subnet D needs 14 addresses, so it wastes 16 addresses. The total wasted addresses are 0+28+28+16=72 addresses.
[/box] - Refer to the exhibit. Considering the addresses already used and having to remain within the 10.16.10.0/24 network range, which subnet address could be assigned to the network containing 25 hosts?
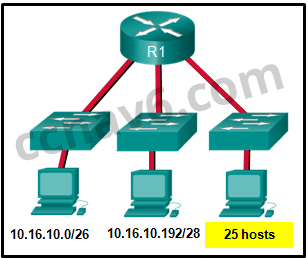
- 10.16.10.160/26
- 10.16.10.128/28
- 10.16.10.64/27*
- 10.16.10.224/26
- 10.16.10.240/27
- 10.16.10.240/28
[box type=”info” align=”alignleft” class=”” width=””]Explain:
Addresses 10.16.10.0 through 10.16.10.63 are taken for the leftmost network. Addresses 10.16.10.192 through 10.16.10.207 are used by the center network.The address space from 208-255 assumes a /28 mask, which does not allow enough host bits to accommodate 25 host addresses.The address ranges that are available include 10.16.10.64/26 and10.16.10.128/26. To accommodate 25 hosts, 5 host bits are needed, so a /27 mask is necessary. Four possible /27 subnets could be created from the available addresses between 10.16.10.64 and 10.16.10.191:
10.16.10.64/27
10.16.10.96/27
10.16.10.128/27
10.16.10.160/27
[/box] - Refer to the exhibit. Given the network address of 192.168.5.0 and a subnet mask of 255.255.255.224 for all subnets, how many total host addresses are unused in the assigned subnets?
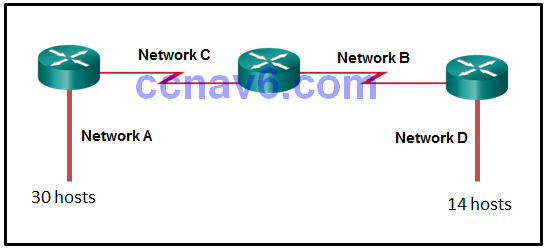
- 64
- 56
- 68
- 60
- 72*
- A network administrator needs to monitor network traffic to and from servers in a data center. Which features of an IP addressing scheme should be applied to these devices?
- random static addresses to improve security
- addresses from different subnets for redundancy
- predictable static IP addresses for easier identification*
- dynamic addresses to reduce the probability of duplicate addresses
[box type=”info” align=”alignleft” class=”” width=””]Explain:
When monitoring servers, a network administrator needs to be able to quickly identify them. Using a predictable static addressing scheme for these devices makes them easier to identify. Server security, redundancy, and duplication of addresses are not features of an IP addressing scheme.
[/box] - Which two reasons generally make DHCP the preferred method of assigning IP addresses to hosts on large networks? (Choose two.)
- It eliminates most address configuration errors.*
- It ensures that addresses are only applied to devices that require a permanent address.
- It guarantees that every device that needs an address will get one.
- It provides an address only to devices that are authorized to be connected to the network.
- It reduces the burden on network support staff.*
[box type=”info” align=”alignleft” class=”” width=””]Explain:
DHCP is generally the preferred method of assigning IP addresses to hosts on large networks because it reduces the burden on network support staff and virtually eliminates entry errors. However, DHCP itself does not discriminate between authorized and unauthorized devices and will assign configuration parameters to all requesting devices. DHCP servers are usually configured to assign addresses from a subnet range, so there is no guarantee that every device that needs an address will get one.
[/box] - A DHCP server is used to assign IP addresses dynamically to the hosts on a network. The address pool is configured with 192.168.10.0/24. There are 3 printers on this network that need to use reserved static IP addresses from the pool. How many IP addresses in the pool are left to be assigned to other hosts?
- 254
- 251*
- 252
- 253
[box type=”info” align=”alignleft” class=”” width=””]Explain:
If the block of addresses allocated to the pool is 192.168.10.0/24, there are 254 IP addresses to be assigned to hosts on the network. As there are 3 printers which need to have their addresses assigned statically, then there are 251 IP addresses left for assignment.
[/box] - Refer to the exhibit. A company is deploying an IPv6 addressing scheme for its network. The company design document indicates that the subnet portion of the IPv6 addresses is used for the new hierarchical network design, with the site subsection to represent multiple geographical sites of the company, the sub-site section to represent multiple campuses at each site, and the subnet section to indicate each network segment separated by routers. With such a scheme, what is the maximum number of subnets achieved per sub-site?
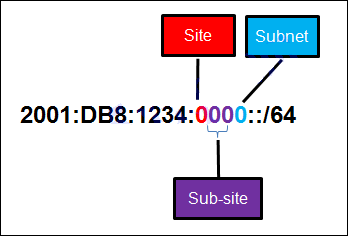
- 0
- 4
- 16*
- 256
[box type=”info” align=”alignleft” class=”” width=””]Explain:
Because only one hexadecimal character is used to represent the subnet, that one character can represent 16 different values 0 through F.
[/box] - What is the prefix for the host address 2001:DB8:BC15:A:12AB::1/64?
- 2001:DB8:BC15
- 2001:DB8:BC15:A*
- 2001:DB8:BC15:A:1
- 2001:DB8:BC15:A:12
[box type=”info” align=”alignleft” class=”” width=””]Explain:
The network portion, or prefix, of an IPv6 address is identified through the prefix length. A /64 prefix length indicates that the first 64 bits of the IPv6 address is the network portion. Hence the prefix is 2001:DB8:BC15:A.
[/box] - Consider the following range of addresses:
2001:0DB8:BC15:00A0:0000:: 2001:0DB8:BC15:00A1:0000:: 2001:0DB8:BC15:00A2:0000:: … 2001:0DB8:BC15:00AF:0000::
The prefix-length for the range of addresses is /60
[box type=”info” align=”alignleft” class=”” width=””]Explain:
All the addresses have the part 2001:0DB8:BC15:00A in common. Each number or letter in the address represents 4 bits, so the prefix-length is /60.[/box] - Match the subnetwork to a host address that would be included within the subnetwork. (Not all options are used.)Question
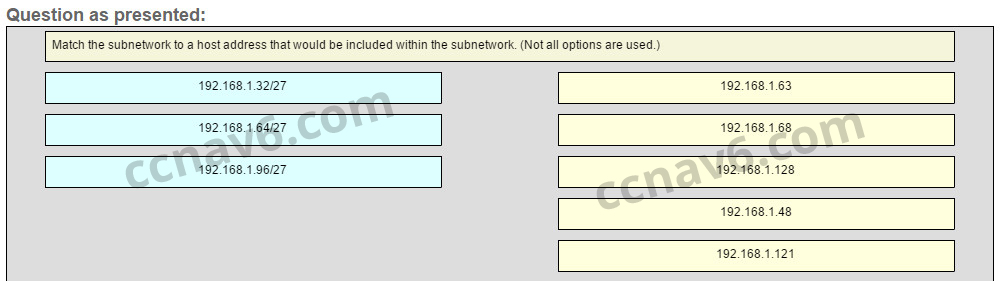
Answer
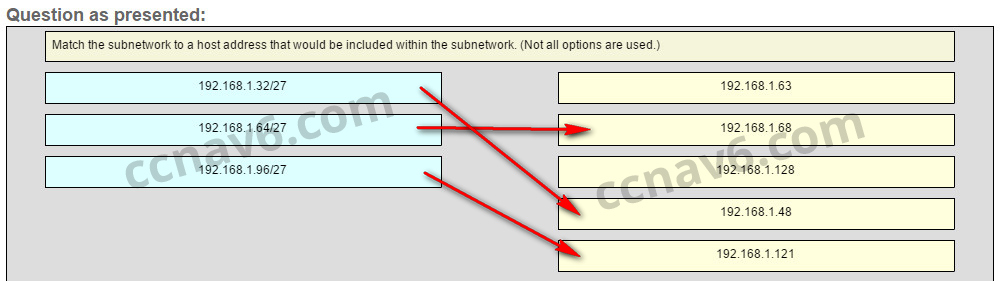 [box type=”info” align=”alignleft” class=”” width=””]Explain:
[box type=”info” align=”alignleft” class=”” width=””]Explain:
Subnet 192.168.1.32/27 will have a valid host range from 192.168.1.33 – 192.168.1.62 with the broadcast address as 192.168.1.63
Subnet 192.168.1.64/27 will have a valid host range from 192.168.1.65 – 192.168.1.94 with the broadcast address as 192.168.1.95
Subnet 192.168.1.96/27 will have a valid host range from 192.168.1.97 – 192.168.1.126 with the broadcast address as 192.168.1.127
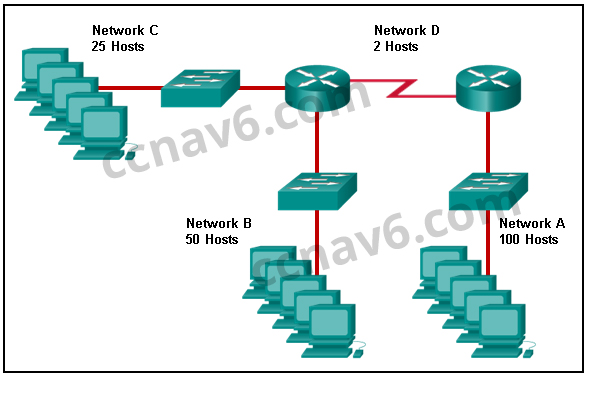
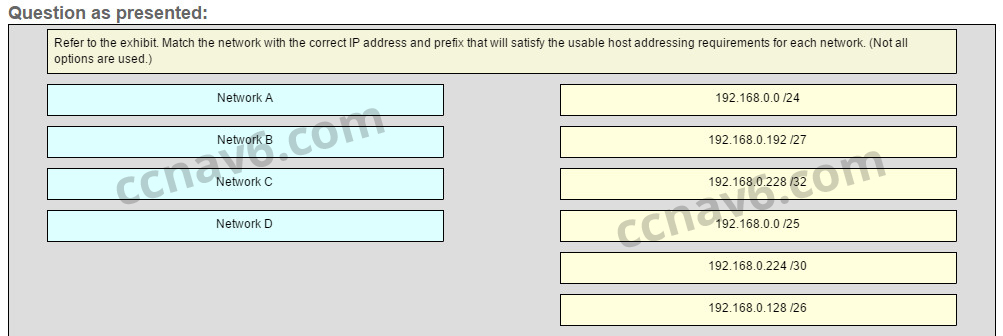
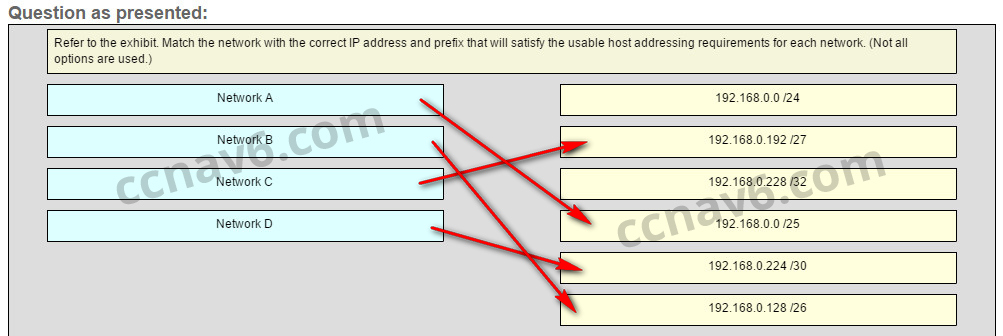
[/box] - Refer to the exhibit. Match the network with the correct IP address and prefix that will satisfy the usable host addressing requirements for each network. (Not all options are used.) From right to left, network A has 100 hosts connected to the router on the right. The router on the right is connected via a serial link to the router on the left. The serial link represents network D with 2 hosts. The left router connects network B with 50 hosts and network C with 25 hosts.
- Question
- Answer
[box type=”info” align=”alignleft” class=”” width=””]Explain:
Network A needs to use 192.168.0.0 /25 which yields 128 host addresses.
Network B needs to use 192.168.0.128 /26 which yields 64 host addresses.
Network C needs to use 192.168.0.192 /27 which yields 32 host addresses.
Network D needs to use 192.168.0.224 /30 which yields 4 host addresses.
[/box] - Question
Older Version
- How many bits are in an IPv4 address?
- 32*
- 64
- 128
- 256
- Which two parts are components of an IPv4 address? (Choose two.)
- subnet portion
- network portion*
- logical portion
- host portion*
- physical portion
- broadcast portion
- What is the prefix length notation for the subnet mask 255.255.255.224?
- /25
- /26
- /27*
- A message is sent to all hosts on a remote network. Which type of message is it?
- limited broadcast
- multicast
- directed broadcast*
- unicast
- What two statements describe characteristics of Layer 3 broadcasts? (Choose two.)
- Broadcasts are a threat and users must avoid using protocols that implement them.
- Routers create broadcast domains. *
- Some IPv6 protocols use broadcasts.
- There is a broadcast domain on each switch interface.
- A limited broadcast packet has a destination IP address of 255.255.255.255.*
- A router will not forward any type of Layer 3 broadcast packet.
- Which network migration technique encapsulates IPv6 packets inside IPv4 packets to carry them over IPv4 network infrastructures?
- encapsulation
- translation
- dual-stack
- tunneling*
- Which two statements are correct about IPv4 and IPv6 addresses? (Choose two.)
- IPv6 addresses are represented by hexadecimal numbers.*
- IPv4 addresses are represented by hexadecimal numbers.
- IPv6 addresses are 32 bits in length.
- IPv4 addresses are 32 bits in length.*
- IPv4 addresses are 128 bits in length.
- IPv6 addresses are 64 bits in length.
- Which IPv6 address is most compressed for the full FE80:0:0:0:2AA:FF:FE9A:4CA3 address?
- FE8::2AA:FF:FE9A:4CA3?
- FE80::2AA:FF:FE9A:4CA3*
- FE80::0:2AA:FF:FE9A:4CA3?
- FE80:::0:2AA:FF:FE9A:4CA3?
- What are two types of IPv6 unicast addresses? (Choose two.)
- multicast
- loopback *
- link-local*
- anycast
- broadcast
- What are three parts of an IPv6 global unicast address? (Choose three.)
- an interface ID that is used to identify the local network for a particular host
- a global routing prefix that is used to identify the network portion of the address that has been provided by an ISP *
- a subnet ID that is used to identify networks inside of the local enterprise site*
- a global routing prefix that is used to identify the portion of the network address provided by a local administrator
- an interface ID that is used to identify the local host on the network*
- An IPv6 enabled device sends a data packet with the destination address of FF02::1. What is the target of this packet?
- all IPv6 DHCP servers *
- all IPv6 enabled nodes on the local link *
- all IPv6 configured routers on the local link *
- all IPv6 configured routers across the network *
- When a Cisco router is being moved from an IPv4 network to a complete IPv6 environment, which series of commands would correctly enable IPv6 forwarding and interface addressing?
- Router# configure terminal
Router(config)# interface fastethernet 0/0
Router(config-if)# ip address 192.168.1.254 255.255.255.0
Router(config-if)# no shutdown
Router(config-if)# exit
Router(config)# ipv6 unicast-routing - Router# configure terminal
Router(config)# interface fastethernet 0/0
Router(config-if)# ipv6 address 2001:db8:bced:1::9/64
Router(config-if)# no shutdown
Router(config-if)# exit
Router(config)# ipv6 unicast-routing* - Router# configure terminal
Router(config)# interface fastethernet 0/0
Router(config-if)# ipv6 address 2001:db8:bced:1::9/64
Router(config-if)# no shutdown - Router# configure terminal
Router(config)# interface fastethernet 0/0
Router(config-if)# ip address 2001:db8:bced:1::9/64
Router(config-if)# ip address 192.168.1.254 255.255.255.0
Router(config-if)# no shutdown
- Router# configure terminal
- Which two ICMP messages are used by both IPv4 and IPv6 protocols? (Choose two.)?
- router solicitation
- route redirection*
- neighbor solicitation
- protocol unreachable*
- router advertisement
- When an IPv6 enabled host needs to discover the MAC address of an intended IPv6 destination, which destination address is used by the source host in the NS message?
- all-node multicast address
- solicited-node multicast address*
- link-local address of the receiver
- global unicast address of the receiver
- When will a router drop a traceroute packet?
- when the router receives an ICMP Time Exceeded message
- when the RTT value reaches zero
- when the host responds with an ICMP Echo Reply message
- when the value in the TTL field reaches zero*
- when the values of both the Echo Request and Echo Reply messages reach zero
- What is indicated by a successful ping to the ::1 IPv6 address?
- The host is cabled properly.
- The default gateway address is correctly configured.
- All hosts on the local link are available.
- The link-local address is correctly configured.
- IP is properly installed on the host.*
- Which two things can be determined by using the ping command? (Choose two.)
- the number of routers between the source and destination device
- the IP address of the router nearest the destination device
- the average time it takes a packet to reach the destination and for the response to return to the source *
- whether or not the destination device is reachable through the network*
- the average time it takes each router in the path between source and destination to respond
- Fill in the blank.
The decimal equivalent of the binary number 10010101 is 149 - 20. Fill in the blank.
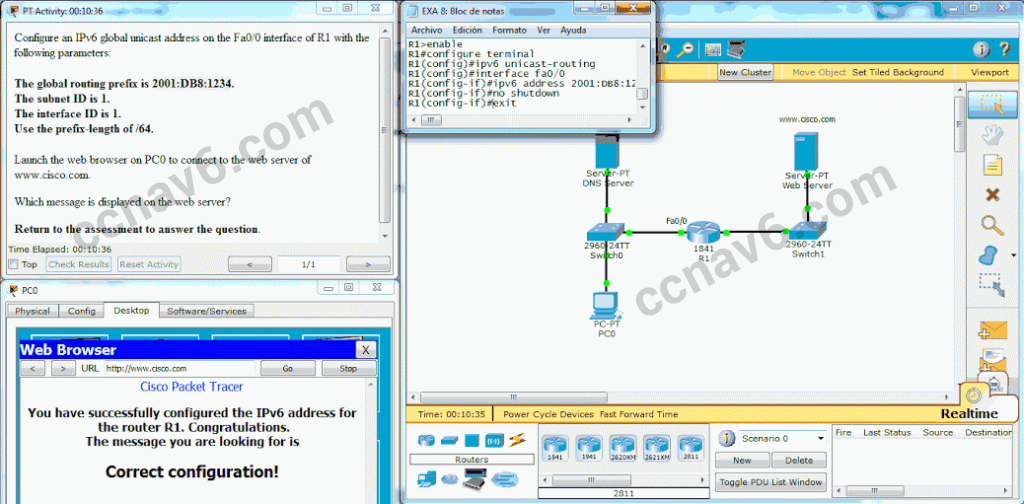
What is the decimal equivalent of the hex number 0x3F? 63* - Open the PT Activity. Perform the tasks in the activity instructions and then answer the question. Which message is displayed on the web server?
- You did it right!
- Correct configuration!*
- IPv6 address configured!
- Successful configuration!
- Match each IPv4 address to the appropriate address category. (Not all options are used.)
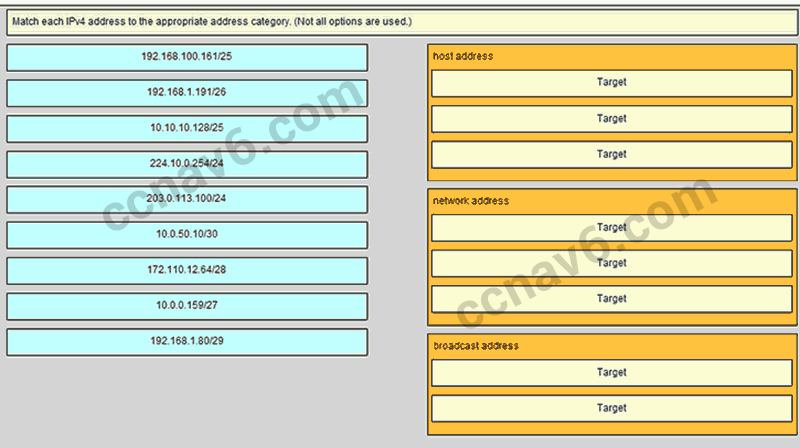
Place the options in the following order:
Host address [A] 192.168.100.161/25 [A]
Host address [B] 203.0.113.100/24 [B]
Host address [C] 10.0.50.10/30 [C]
Network address [D] 192.168.1.80/29 [D]
Network address [E] 172.110.12.64/28 [E]
Network address [F] 10.10.10.128/25 [F]
Broadcast address [G] 10.0.0.159/27 [G]
Broadcast address [H] 192.168.1.191/26 [H]
- Match each description with an appropriate IP address. (Not all options are used)
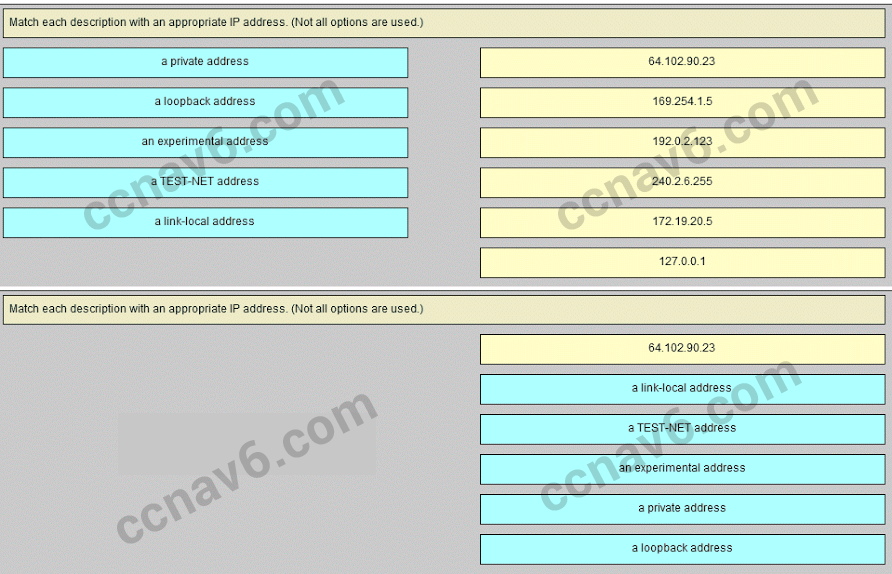
169.254.1.5 -> a link-local address
192.0.2.153 -> a TEST-NET address
240.2.6.255 -> an experimental address
172.19.20.5 -> a private address
127.0.0.1 -> a loopback address - Match each description with an appropriate IP address. (Not all options are used.)
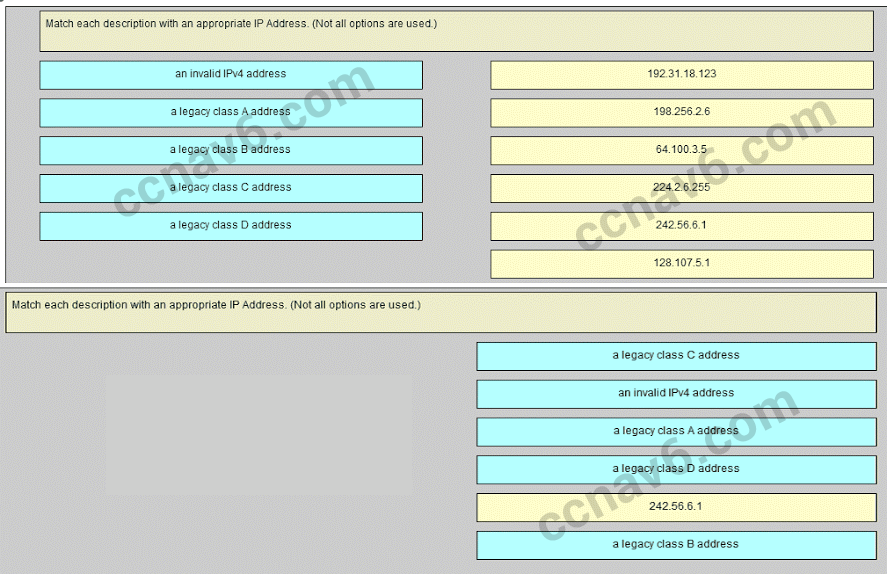
192.31.18.123 -> a legacy class C address
198.256.2.6 -> an invalid IPv4 address
64.100.3.5 -> a legacy class A address
224.2.6.255 -> a legacy class D address
128.107.5.1 -> a legacy class B address - Which three addresses could be used as the destination address for OSPFv3 messages? (Choose three.)
- FF02::A
- FF02::1:2
- 2001:db8:cafe::1
- FE80::1*
- FF02::5*
- FF02::6*
- What is the result of connecting multiple switches to each other?
- The number of broadcast domains is increasing.
- The number of collision domains decreases.
- The size of the broadcast domain is increasing.*
- The size of the collision domain decreases.
- Which wildcard mask would be used to advertise the 192.168.5.96/27 network as part of an OSPF configuration?
- 255.255.255.224
- 0.0.0.32
- 255.255.255.223
- 0.0.0.31*
Download PDF File below:
[sociallocker id=”8425″]
