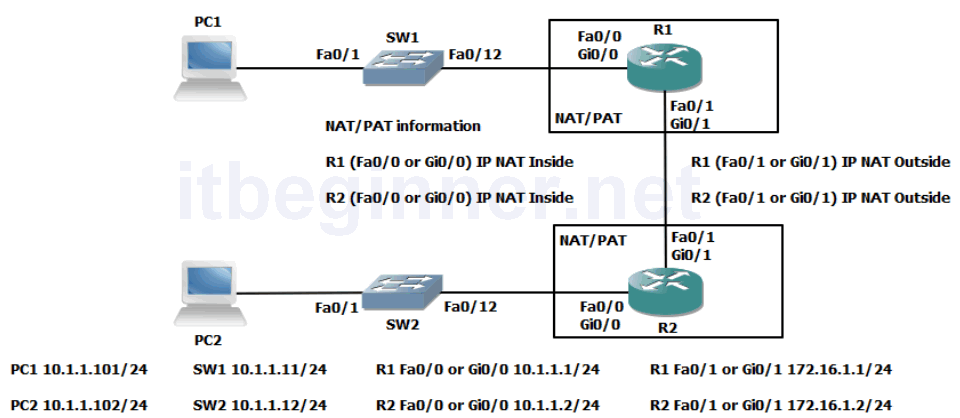
Visual Topology
Command Lis
| Command | Description |
|---|---|
| Access-list acl id permit network wildcard mask | Creates a standard IP access control list (ACL) |
| Debug IP ICMP | Displays real-time ICMP traffic activity |
| IP nat inside | Configures an interface as NAT inside |
| IP nat inside source list acl id pool pool name | Dynamic source NAT rule that translates candidates permitted by an ACL to a pool of global addresses. |
| IP nat inside source list acl id interface name overload | Dynamic source PAT rule which translates candidates permitted by an ACL to the IP address of the IP nat outside interface |
| IP nat outside | Configures an interface as NAT outside |
| IP nat pool pool name start ip end ip netmask mask | Configures a pool of global addresses |
| IP route network mask [next hop/exitinterface] | Creates a static route to a remote network |
| Sh ip int brief | Displays interface status and ip information |
| Show ip route | Displays a list of the best paths to networks |
| Show users | Information regarding active line connections |
| [no] shutdown | Disable or enables an interface |
| Telnet ip address / hostname | Telnet to a remote device |
| Terminal monitor | Redirects debugging output to your telnet session instead of the default console port |
| Undebug all | Disable all debugging commands |
Physical Topology Diagram
- Task 1: Defining static IP addresses and setting a static default route.
- Task 2: Configure NAT.
- Task 3: Configure PAT.
Lab 2-2: Internet connections
Task 1: Defining static IP addresses and setting a static default route.
Step 1: Access the CLI of the router and verify the current status of the ethernet interfaces using the show ip int brief command.
The first ethernet interface should already be configured with an IP address and a status of up/up, if not rectify this.
Step 2: Enter the configuration mode of the second Ethernet interface (fa0/1 or gi0/1), place the interface into a disable state and then manually assign an IP address which is listed in the Visual Topology diagram.
Step 3: Enable the second Ethernet interface and Ping the other router, remember both sides of the link will need to be configured and enabled before the Ping will be successful.
Step 4: Execute the command which allows you to view the contents of the routing table.
R1#sh ip route
or
R2#sh ip route
How many entries would you expect to see? Can you see any remote networks?
Task 2: Configure NAT.
Step 1: Access the CLI on the Router
Step 2: Configure a standard IP ACL using an ACL id of 1 and permit any device on subnet 10.1.1.0 /24
R1(config)#access-list 1 permit 10.1.1.0 0.0.0.255
or
R2(config)#access-list 1 permit 10.1.1.0 0.0.0.255
This ACL will be used to identify which source IP addresses are going to be translated using NAT, and this example allows any device from the 10.1.1.0 subnet.
Step 3: Create a dynamic NAT address pool, this will hold a list of inside global addresses.
Use this table and parameters on Router R1 only
| Pool name | NAT-POOL |
| Starting IP address | 192.168.1.1 |
| Ending IP address | 192.168.1.14 |
| Network mask | 255.255.255.240 |
R1(config)#ip nat pool NAT-POOL 192.168.1.1 192.168.1.14 netmask 255.255.255.240
Use this table and parameters on Router R2 only
| Pool name | NAT-POOL |
| Starting IP address | 192.168.1.1 |
| Ending IP address | 192.168.1.14 |
| Network mask | 255.255.255.240 |
R2(config)#ip nat pool NAT-POOL 192.168.2.1 192.168.2.14 netmask 255.255.255.240
Stop…..Have you configured the right set of parameters for your Router!
Step 4: Linking the nat pool to the ACL.
R1(config)#ip nat inside source list 1 pool NAT-POOL
or
R2(config)#ip nat inside source list 1 pool NAT-POOL
NB. Nat Pool names are case-sensitive
Step 5: Before any NAT translations occur we must identify at least two interfaces to be our inside and outside.
Source IP address will be translated when traffic traverses between the inside and outside interfaces and destination IP addresses will be translated in the opposite direction between the outside and inside.
Interface fa0/0 or gi0/0 will be our inside interface
Interface fa0/1 or gi0/1 will be our outside interface
Assign the following commands to the relevant interfaces.
The example shown illustrates the commands required on Router R1 which is a 2901 device, you may need to use fa0/0 and fa0/1 if you are using a 2811 device.
R1(config)#int gi0/0 R1(config-if)#ip nat inside R1(config-if)#int gi0/1 R1(config-if)#ip nat outside
Step6: When we ping from PC1 to R2 or PC2 to R1 our original IP address will be translated from a 10.1.1.x to a 192.168.x.x address (x denotes a variable depending on the direction of the traffic)
Therefore we need to configure a static route back to the 192.168.x.x network.
R1 only... R1(config)#ip route 192.168.2.0 255.255.255.0 172.16.1.2 R2 only... R2(config)#ip route 192.168.1.0 255.255.255.0 172.16.1.1
Use the appropriate command to verify that they have been added to the routing table.
R1#sh ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
******some output missing******
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.1.1.0/24 is directly connected, GigabitEthernet0/0
L 10.1.1.1/32 is directly connected, GigabitEthernet0/0
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
C 172.16.1.0/24 is directly connected, GigabitEthernet0/1
L 172.16.1.1/32 is directly connected, GigabitEthernet0/1
S 192.168.2.0/24 [1/0] via 172.16.1.2
Step 7: We have now configured all of the NAT components and a static route to the translated addresses, the next stage is to test our configuration.
From your PC check you still have a valid 10.1.1.11 or 10.1.1.12 address using ipconfig/all from the command shell (cmd).
PC1 will require a default gateway address of 10.1.1.1
and
PC2 will require a default gateway address of 10.1.1.2
Verify and rectify if necessary.
Check you can ping your default gateway from your PC
If you are having problems open the command shell (cmd) and type in the following statements.
On PC1 only... route -p add 10.1.1.0 mask 255.255.255.0 10.1.1.1 route -p add 172.16.1.0 mask 255.255.255.0 10.1.1.1 On PC2 only... route -p add 10.1.1.0 mask 255.255.255.0 10.1.1.2 route -p add 172.16.1.0 mask 255.255.255.0 10.1.1.2
Your classroom PC might be fitted with dual interface cards and we need to direct our traffic out of the correct interface.
Step 7: Testing NAT translation.
Traffic will need to traverse across the inside and outside interfaces before any entries will be seen in the IP NAT Translation table.
From you classroom PC ping the IP address of the outside interface on the corresponding router.
Examples From PC1 ping 172.16.1.2 (this is the outside interface on R2) From PC2 ping 172.16.1.1 (this is the outside interface on R1) Check the contents of the IP nat table using the following command. sh ip nat trans (remember show commands run from privilege EXEC mode) Example from R1 R1#sh ip nat trans Pro Inside global Inside local Outside local Outside global icmp 192.168.1.1:10 10.1.1.11:10 172.16.1.2:10 172.16.1.2:10 icmp 192.168.1.1:11 10.1.1.11:11 172.16.1.2:11 172.16.1.2:11 icmp 192.168.1.1:12 10.1.1.11:12 172.16.1.2:12 172.16.1.2:12 icmp 192.168.1.1:9 10.1.1.11:9 172.16.1.2:9 172.16.1.2:9
Task 3: Configure PAT.
Step 1: Removing the previous NAT configuration so we can apply PAT using the same pair of interfaces.
R1 only... Type in the following commands. R1(config)#no ip nat pool NAT-POOL 192.168.1.1 192.168.1.14 netmask 255.255.255.240 R1(config)#no ip nat inside source list 1 pool NAT-POOL R2 only... Type in the following commands. R2(config)#no ip nat pool NAT-POOL 192.168.2.1 192.168.2.14 netmask 255.255.255.240 R2(config)#no ip nat inside source list 1 pool NAT-POOL
These commands remove the dynamic pool of addresses used by NAT and the link between the ACL and NAT Pool.
We will still use the existing ACL and IP NAT Inside/outside interface statements when configuring PAT.
Step 2: Configure a dynamic PAT rule which translates your 10.1.1.0 subnet to the IP address configured on the Routers outside interface.
ip nat inside source list 1 interface fa0/1 overload
Or
ip nat inside source list 1 interface gi0/1 overload
What does the list 1 part of the command relate to?
What does the key word overload do?
Step 3: Verifying your configuration by Pinging the IP address of the other Routers outside interface.
Use the appropriate command to view the contents of the IP translation table.
Do you see any output differences between the previously configured dynamic NAT pool and the newly configured PAT function? Pay attention to the inside global address!
Describe the following NAT/PAT terms Inside local Inside global Outside global Outside local
Step 4: Once you are satisfied that PAT is configured correctly we can now remove it from the system, remember to remove all components and you will need to be in the right configuration mode to execute these commands.
no ip nat inside no ip nat outside no access-list 1 no ip nat inside source list 1 interface fa0/1 overload or no ip nat inside source list 1 interface gi0/1 overload
Step 5: Shutdown the fa0/1 or gi0/1 interface.
fa0/1 if you are using a 2811 router and gi0/1 if you are using a 2901 router
Step 6: Save your current configuration.
Lab Answer Keys:
[sociallocker id=”4139″]
Task 1: Defining static IP addresses and setting a static default route.
Step 2: Enter the configuration mode of the second Ethernet interface (fa0/1 or gi0/1), place the interface into a disable state and then manually assign an IP address which is listed in the Visual Topology diagram.
R1 only..... R1(config-if)#ip address 172.16.1.1 255.255.255.0 R1(config-if)#no shut R2 only..... R2(config-if)#ip address 172.16.1.2 255.255.255.0 R2(config-if)#no shut
Step 4: Execute the command which allows you to view the contents of the routing table.
R1#sh ip route
or
R2#sh ip route
How many entries would you expect to see? Can you see any remote networks?
2, subnets 10.1.1.0 /24 and 172.16.1.0 /24 both local to the router
The router will calculate these subnets based on the active IP addresses configured on the local interfaces.
No remote networks are present until a static route or dynamic routing protocols are configured.
Task 2: Configure NAT.
Step 2: Configure a standard IP ACL using an ACL id of 1 and permit any device on subnet 10.1.1.0 /24
R1(config)#access-list 1 permit 10.1.1.0 0.0.0.255
or
R2(config)#access-list 1 permit 10.1.1.0 0.0.0.255
This ACL will be used to identify which source IP addresses are going to be translated using NAT, and this example allows any device from the 10.1.1.0 subnet.
Step 3: Create a dynamic NAT address pool, this will hold a list of inside global addresses.
Use this table and parameters on Router R1 only
| Pool name | NAT-POOL |
| Starting IP address | 192.168.1.1 |
| Ending IP address | 192.168.1.14 |
| Network mask | 255.255.255.240 |
R1(config)#ip nat pool NAT-POOL 192.168.1.1 192.168.1.14 netmask 255.255.255.240
Use this table and parameters on Router R2 only
| Pool name | NAT-POOL |
| Starting IP address | 192.168.1.1 |
| Ending IP address | 192.168.1.14 |
| Network mask | 255.255.255.240 |
R2(config)#ip nat pool NAT-POOL 192.168.2.1 192.168.2.14 netmask 255.255.255.240
Stop…..Have you configured the right set of parameters for your Router!
Step 4: Linking the nat pool to the ACL.
R1(config)#ip nat inside source list 1 pool NAT-POOL
or
R2(config)#ip nat inside source list 1 pool NAT-POOL
NB. Nat Pool names are case-sensitive
Step 5: Before any NAT translations occur we must identify at least two interfaces to be our inside and outside.
Source IP address will be translated when traffic traverses between the inside and outside interfaces and destination IP addresses will be translated in the opposite direction between the outside and inside.
Interface fa0/0 or gi0/0 will be our inside interface Interface fa0/1 or gi0/1 will be our outside interface
Assign the following commands to the relevant interfaces.
The example shown illustrates the commands required on Router R1 which is a 2901 device, you may need to use fa0/0 and fa0/1 if you are using a 2811 device.
R1(config)#int gi0/0 R1(config-if)#ip nat inside R1(config-if)#int gi0/1 R1(config-if)#ip nat outside
Step6: When we ping from PC1 to R2 or PC2 to R1 our original IP address will be translated from a 10.1.1.x to a 192.168.x.x address (x denotes a variable depending on the direction of the traffic)
Therefore we need to configure a static route back to the 192.168.x.x network.
R1 only... R1(config)#ip route 192.168.2.0 255.255.255.0 172.16.1.2 R2 only... R2(config)#ip route 192.168.1.0 255.255.255.0 172.16.1.1
Use the appropriate command to verify that they have been added to the routing table.
R1#sh ip route Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP ******some output missing****** Gateway of last resort is not set 10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks C 10.1.1.0/24 is directly connected, GigabitEthernet0/0 L 10.1.1.1/32 is directly connected, GigabitEthernet0/0 172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks C 172.16.1.0/24 is directly connected, GigabitEthernet0/1 L 172.16.1.1/32 is directly connected, GigabitEthernet0/1 S 192.168.2.0/24 [1/0] via 172.16.1.2
Step 7: We have now configured all of the NAT components and a static route to the translated addresses, the next stage is to test our configuration.
From your PC check you still have a valid 10.1.1.11 or 10.1.1.12 address using ipconfig/all from the command shell (cmd).
PC1 will require a default gateway address of 10.1.1.1
and
PC2 will require a default gateway address of 10.1.1.1
Verify and rectify if necessary.
Check you can ping your default gateway from your PC
If you are having problems open the command shell (cmd) and type in the following statements.
On PC1 only... route -p add 10.1.1.0 mask 255.255.255.0 10.1.1.1 route -p add 172.16.1.0 mask 255.255.255.0 10.1.1.1 On PC2 only... route -p add 10.1.1.0 mask 255.255.255.0 10.1.1.2 route -p add 172.16.1.0 mask 255.255.255.0 10.1.1.2
Your classroom PC might be fitted with dual interface cards and we need to direct our traffic out of the correct interface.
Step 7: Testing NAT translation.
Traffic will need to traverse across the inside and outside interfaces before any entries will be seen in the IP NAT Translation table.
From you classroom PC ping the IP address of the outside interface on the corresponding router.
Examples
From PC1 ping 172.16.1.2 (this is the outside interface on R2) From PC2 ping 172.16.1.1 (this is the outside interface on R1) Check the contents of the IP nat table using the following command. sh ip nat trans (remember show commands run from privilege EXEC mode) Example from R1 R1#sh ip nat trans Pro Inside global Inside local Outside local Outside global icmp 192.168.1.1:10 10.1.1.11:10 172.16.1.2:10 172.16.1.2:10 icmp 192.168.1.1:11 10.1.1.11:11 172.16.1.2:11 172.16.1.2:11 icmp 192.168.1.1:12 10.1.1.11:12 172.16.1.2:12 172.16.1.2:12 icmp 192.168.1.1:9 10.1.1.11:9 172.16.1.2:9 172.16.1.2:9
Task 3: Configure PAT.
Step 1: Removing the previous NAT configuration so we can apply PAT using the same pair of interfaces.
R1 only... Type in the following commands. R1(config)#no ip nat pool NAT-POOL 192.168.1.1 192.168.1.14 netmask 255.255.255.240 R1(config)#no ip nat inside source list 1 pool NAT-POOL R2 only... Type in the following commands. R2(config)#no ip nat pool NAT-POOL 192.168.2.1 192.168.2.14 netmask 255.255.255.240 R2(config)#no ip nat inside source list 1 pool NAT-POOL
These commands remove the dynamic pool of addresses used by NAT and the link between the ACL and NAT Pool.
We will still use the existing ACL and IP NAT Inside/outside interface statements when configuring PAT.
Step 2: Configure a dynamic PAT rule which translates your 10.1.1.0 subnet to the IP address configured on the Routers outside interface.
R(config)#ip nat inside source list 1 interface fa0/1 overload
Or
R(config)#ip nat inside source list 1 interface gi0/1 overload
What does the list 1 part of the command relate to?
Links to the ACL id which identifies which candidates are allowed
What does the key word overload do?
Turns PAT on
Step 3: Verifying your configuration by Pinging the IP address of the other Routers outside interface.
Use the appropriate command to view the contents of the IP translation table.
R#sh ip nat translation
Do you see any output differences between the previously configured dynamic NAT pool and the newly configured PAT function? Pay attention to the inside global address!
The inside global address will be the same value for all translations.
Describe the following NAT/PAT terms
Inside local
Original address on the inside interface (usually private)
Inside global
Translated address which appears to the outside network (usually public)
Outside global
Address we are trying to contact (usually public)
Outside local
A destination address which is hidden behind a NAT or PAT function (usually private)
Step 4: Once you are satisfied that PAT is configured correctly we can now remove it from the system, remember to remove all components and you will need to be in the right configuration mode to execute these commands.
R(config-if)#no ip nat inside R(config-if)#no ip nat outside R(config)#no access-list 1 R(config)#no ip nat inside source list 1 interface fa0/1 overload or R(config)#no ip nat inside source list 1 interface gi0/1 overload
Step 5: Shutdown the fa0/1 or gi0/1 interface.
fa0/1 if you are using a 2811 router and gi0/1 if you are using a 2901 router
R(config-if)#shut
Step 6: Save your current configuration.
R#copy run start
[/sociallocker]
