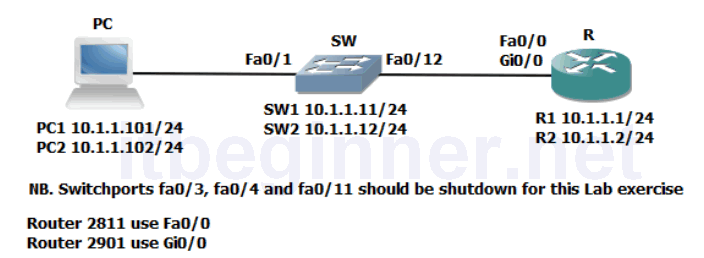
Visual Topology
Command Lis
| Command | Description |
|---|---|
| Access-class acl id [in/out] | Access-class acl id [in/out] |
| Access-list number permit ip address wildcard mask | Creates a standard IP access control list (ACL) |
| Banner login | Message will be displayed just before login |
| Crypto key generate rsa | Generates a RSA Public/Private key pair used for asymmetrical encryption or authentication |
| Enable secret | Protects the privilege mode. Password is either put through a MD5 or SHA2 hashing algorithm dependant on the version of the IOS being used. |
| IP domain-name name | Applies a system domain name which is required for the process of generating the cryptographic keys |
| IP ssh version [1/2] | Specifies the version of SSH |
| line vty 0 4 | Enters the configuration mode to manage remote telnet and ssh sessions. |
| login | Login process for the console or VTY lines, requires password command before the service will start. |
| login local | Login process for the console or VTY lines using a local authentication database |
| logout | Exits EXEC mode |
| Password password | Assigns a password to the console or VTY lines |
| show access-list | Displays the details of any ACLs configured on the device |
| show users | Display any users currently accessing the system via the console or VTY lines |
| ssh -l username ip address | Allows the system to remotely access a device via a ssh session. |
| Transport input [telnet / ssh / all] | Specifies which line protocols are permitted on the VTY lines, default is all. |
| username username secret password | Creates an entry into the local user database, can be used with ssh and login local functions. |
Switches and routers behave differently when set to factory defaults.
Switches will allow all communications between the connecting devices, whereby routers require some initial configuration before any traffic traverses between any two interfaces, both switches and routers will require IP setup before you can remotely manage them via telnet, ssh or snmp.
It is also advisable to protect the privilege EXEC mode, console port and VTY lines using either a password or the credentials of a user.
Physical Topology Diagram
- Task 1: Device password protection.
- Task 2: Remote access using Telnet and SSH.
- Task 3: Limiting remote access based on source IP addresses.
- Task 4: Creating a login banner page.
Lab 3-1: Improving Device Security
Task 1: Device password protection.
Step 1: Access the console port of the router.
Step 2: Secure the console port with the password cisco
(please don’t use any maverick passwords, only those specified in the lab instructions and passwords are case-sensitive)
Step 3: Verify your password by exiting from the line con 0 mode and then the user EXEC mode using the End and Exit commands.
Step 4: Enter the console password to return to user EXEC mode.
Step 5: Create a local user account with a username of ccna and a secret password of cisco
Step 6: Change the security method used on the console port to now prompt the administrator for a username and password.
Important…Step 5 must be completed before Step 6 otherwise you will lock yourself out of the system.
Step 7: Verify the security change by logging out of the system, you will notice this time you are asked for a username and password instead of just a password which doesn’t identify the person accessing the system.
Task 2: Remote access using Telnet and SSH.
Using telnet (insecure) and ssh (secure) protocols allow administrators to access their devices remotely, providing IP connectivity exists between the telnet/ssh client and the telnet/ssh server.
In this task we are going to configure our router to support telnet and ssh sessions via the VTY lines.
Step 1: Access the router CLI and navigate to the VTY configuration mode, enter a command which forces the administrator to provide a username and password.
Hint: Used on the console port in the previous task.
Step 2: From the your PCs desktop launch the PuTTy application.
PuTTy is a freely available application which supports both telnet and ssh.
Select the connection type radio button for telnet and type in the IP address of routers interface, in other words your default gateway.
R1 10.1.1.1 or R2 10.1.1.2
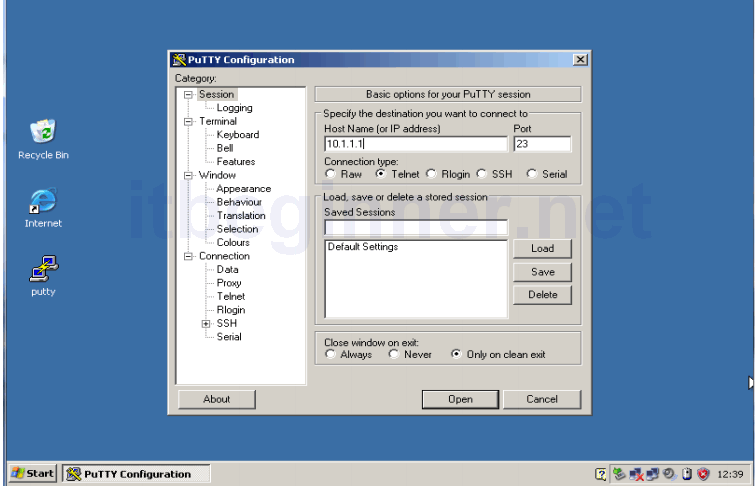
Click open and enter the username ccna and password cisco
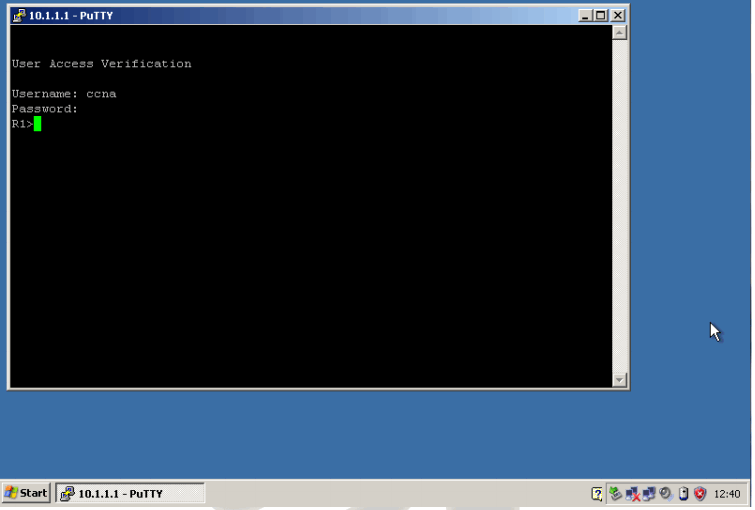
Enter the command to gain access to the privilege mode and type in the secret password of cisco
Execute the sh users command the output should look like the image below
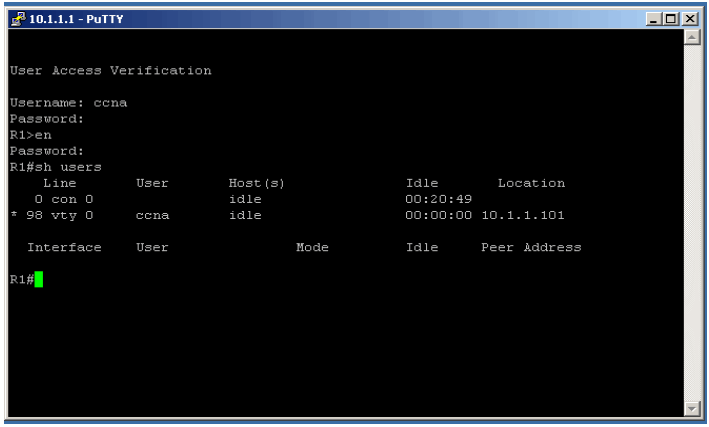
The output of the sh users command indicates that a user is accessing the device via the line VTY 0 with a username of ccna and a source IP address of 10.1.1.101
Step 3: Telnet provides a method of remote administration but unfortunately when you type in the authentication details, the username and password are sent in clear text therefore telnet should only be used on trusted interfaces or via a VPN encrypted tunnel. SSH version 2 is the preferred method because it can provide authentication and data protection via an encrypted channel.
To configure SSH we need to setup a domain name, generate our RSA public/private key pairs, recommended we support only version 2 and make sure that the VTY lines also support the SSH protocol.
Run the following commands from global configuration mode.
IP domain-name cisco.com
crypto key generate rsa
change the modulus size to 1024 when prompted (ssh version 2 needs a minimum modulus size of 768 bits or greater)
IP ssh version 2
Optional, if you decided that your company policy dictates that all remote connections must be secure then you could use the following command on the VTY lines.
transport input ssh
This command disables all other protocols excluding ssh
Step 4: Check that ssh is working by opening a PuTTy session to your router from your PC but this time under the connection type select the ssh radio button, type in the IP address of the router and open the connection.
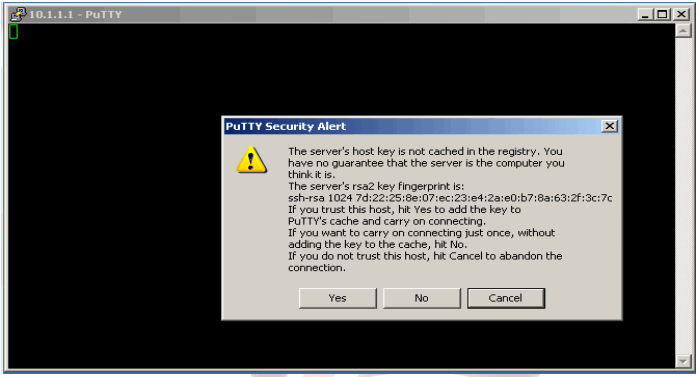
If you receive the following security alert click yes
Login as requested using the local account credentials
Enter privilege mode
Execute the following two show commands
sh users
sh ssh
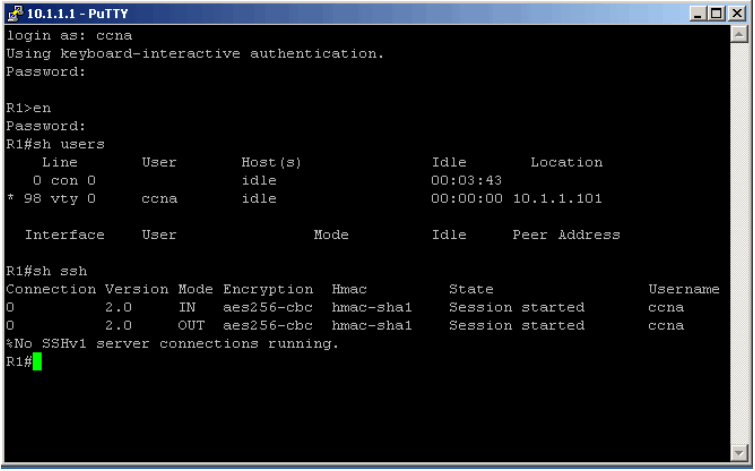
The output states that we are accessing the system via line VTY 0 and ssh version is being used.
If you decided to try the optional transport input ssh please reset this back to its default condition, transport input all once again enabling telnet and ssh at the same time.
What are the ports numbers used by telnet and ssh?
What command generates the Public/Private key pairs and what was the default modulus size?
Task 3: Limiting remote access based on source IP addresses.
It is possible to restrict which host or subnet a device is on when managing remote access. Standard IP ACLs can be used to identify the source IP address of a ssh or telnet client.
Step 1: Check you can still telnet or ssh into your router from your PC before you start the next step.
Step 2: Check the IP address of your PC and make a note of it below.
Step 3: Access the CLI on the router and navigate to the global configuration mode, this is where you will need to create a standard IP ACL which allows only your PC to telnet or ssh into the router, please use an ACL id of 2.
access-list 2 permit 10.1.1.101 0.0.0.0
or
access-list 2 permit 10.1.1.102 0.0.0.0
What does the wildcard mask 0.0.0.0 do ? Can you think of an alternative way of writing the ACL.
Step 4: Apply this ACL to the VTY lines using the appropriate command, use the command list if you are unsure.
Step 5: Telnet or ssh into your router from your PC, this should still work even after you have applied the ACL.
Step 6: Change the IP address on your PC
PC1 10.1.1.133/24
PC2 10.1.1.144/24
Now try and telnet or ssh to your router, should you be successful?
Step 7: Reset your PC to its original IP address, verify you can telnet or ssh to the router before moving on to the next task.
Task 4: Creating a login banner page.
Most systems have a mandatory security message displayed to anybody accessing the system.
Step 1: Access the router CLI and create a login message which advises only authorised users are permitted to access the system.
Hint: Remember to use delimiting characters to identify the beginning and end of the displayed message.
Step 2: Telnet or ssh to check your login message.
Step 3: Save your running-config
Lab Answer Keys:
[sociallocker id=”4139″]
Task 1: Device password protection.
Step 1: Access the console port of the router.
R#conf t
R(config)#line con 0
R(config-line)#
Step 2: Secure the console port with the password cisco
R(config-line)#password cisco
R(config-line)#login
(please don’t use any maverick passwords, only those specified in the lab instructions and passwords are case-sensitive)
Step 3: Verify your password by exiting from the line con 0 mode and then the user EXEC mode using the End and Exit commands.
Step 4: Enter the console password to return to user EXEC mode.
Step 5: Create a local user account with a username of ccna and a secret password of cisco
R(config)#username ccna secret cisco
Step 6: Change the security method used on the console port to now prompt the administrator for a username and password.
R(config)#line con 0
R(config-line)#login local
Important…Step 5 must be completed before Step 6 otherwise you will lock yourself out of the system.
Step 7: Verify the security change by logging out of the system, you will notice this time you are asked for a username and password instead of just a password which doesn’t identify the person accessing the system.
Task 2: Remote access using Telnet and SSH.
Using telnet (insecure) and ssh (secure) protocols allow administrators to access their devices remotely, providing IP connectivity exists between the telnet/ssh client and the telnet/ssh server.
In this task we are going to configure our router to support telnet and ssh sessions via the VTY lines.
Step 1: Access the router CLI and navigate to the VTY configuration mode, enter a command which forces the administrator to provide a username and password.
R(config)#line vty 0 4
R(config-line)#login local
Hint: Used on the console port in the previous task.
Step 3: Telnet provides a method of remote administration but unfortunately when you type in the authentication details, the username and password are sent in clear text therefore telnet should only be used on trusted interfaces or via a VPN encrypted tunnel. SSH version 2 is the preferred method because it can provide authentication and data protection via an encrypted channel.
To configure SSH we need to setup a domain name, generate our RSA public/private key pairs, recommended we support only version 2 and make sure that the VTY lines also support the SSH protocol.
Run the following commands from global configuration mode.
R(config)#IP domain-name cisco.com
R(config)#crypto key generate rsa
change the modulus size to 1024 when prompted (ssh version 2 needs a minimum modulus size of 768 bits or greater)
R(config)#IP ssh version 2
Optional, if you decided that your company policy dictates that all remote connections must be secure then you could use the following command on the VTY lines.
R(config)#line vty 0 4
R(config-line)#transport input ssh
This command disables all other protocols excluding ssh
Step 4: Check that ssh is working by opening a PuTTy session to your router from your PC but this time under the connection type select the ssh radio button, type in the IP address of the router and open the connection.
If you receive the following security alert click yes
Login as requested using the local account credentials
Username ccna password cisco
Enter privilege mode
R>enable
Execute the following two show commands
R#sh users
R#sh ssh
The output states that we are accessing the system via line VTY 0 and ssh version is being used.
If you decided to try the optional transport input ssh please reset this back to its default condition, transport input all once again enabling telnet and ssh at the same time.
R(config)#line vty 0 4
R(config-line)#transport input all
What are the ports numbers used by telnet and ssh?
Telnet TCP 23
SSH TCP 22
What command generates the Public/Private key pairs and what was the default modulus size?
R(config)#crypto key generate rsa
Default modulus 512 bits (Cisco now recommend a minimum of 2048 bits)
Task 3: Limiting remote access based on source IP addresses.
It is possible to restrict which host or subnet a device is on when managing remote access. Standard IP ACLs can be used to identify the source IP address of a ssh or telnet client.
Step 2: Check the IP address of your PC and make a note of it below.
ipconfig /all
Step 3: Access the CLI on the router and navigate to the global configuration mode, this is where you will need to create a standard IP ACL which allows only your PC to telnet or ssh into the router, please use an ACL id of 2.
R(config)#access-list 2 permit 10.1.1.101 0.0.0.0
or
R(config)#access-list 2 permit 10.1.1.102 0.0.0.0
What does the wildcard mask 0.0.0.0 do ? Can you think of an alternative way of writing the ACL.
Matches all 32 bits to identify an individual host.
Step 4: Apply this ACL to the VTY lines using the appropriate command, use the command list if you are unsure.
R(config)#line vty 0 4
R(config-line)#access-class 2 in
Step 6: Change the IP address on your PC
PC1 10.1.1.133/24
PC2 10.1.1.144/24
Now try and telnet or ssh to your router, should you be successful?
NO the ACL will block your access
Task 4: Creating a login banner page.
Most systems have a mandatory security message displayed to anybody accessing the system.
Step 1: Access the router CLI and create a login message which advises only authorised users are permitted to access the system.
Example
R(config)#banner login # authorised access only! #
Hint: Remember to use delimiting characters to identify the beginning and end of the displayed message.
Step 3: Save your running-config
R#copy run start
[/sociallocker]
