Visual Topology
Command Lis
| Command | Description |
|---|---|
| [no] cdp enable | Enables or disables CDP on an interface |
| show cdp neighbors [detail] | Displays CDP neighbours |
| Show mac-address | Displays the contents of the switches mac-address table. |
| show interfaces | Displays interface statistics |
| show interface status | Displays interface status |
| show port-security interface interface | Displays port security configured on an interface |
| show port-security address | Displays port-security MAC addresses |
| [no] shutdown | Disables or enable a switchport or interface |
| switchport mode access | Sets the switchport into access mode supporting only one data and one voice vlan |
| switchport port-security | Enables port-security |
| switchport port-security mac-address | Sets a static secure MAC address |
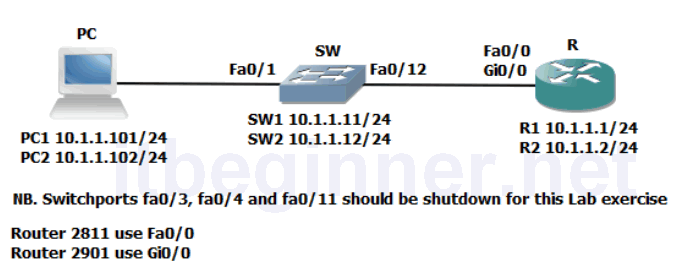
Physical Topology Diagram
- Task 1: Managing unused ports on a Switch.
- Task 2: Using Switchport port-security.
- Task 3: Disable unused services.
Lab 3-2: Device Hardening
Task 1: Managing unused ports on a Switch.
Step 1: Access the CLI on your switch
Step 2: Ensure that the interface connecting your switch to your Router is enabled by using
the no shutdown command, remember to be in the right configuration mode?
Task 2: Using Switchport port-security.
Step 1: Access the CLI on your Router
Step 2: Identify the MAC address of the interface used to connect to y our switch.
What command could be used to achieve step 2 ?
Once you know the MAC address of the interface make a note of it below.
MAC Address:
Step 3: Enter the configuration mode which will allow you to change the interface parameters on Fa0/0 or Gi0/0.
Shutdown the interface and set the MAC address to the following value using these commands:
Rx(config-if)#Shut
Rx(config-if)#mac-address 0000.0C12.ABCD
Step 4: Enable the interface and generate some traffic by pinging the IP address of your switch.
Step 5: Access the switches CLI.
What command could we use to check the MAC address of the attached router?
Step 6: While still accessing the CLI on the switch, shutdown the interface fa0/12
Step 7: Enable switchport security using the following commands:
SWx(config-if)#switchport mode access
SWx(config-if)#switchport port-security
SWx(config-if)#switchport port-security mac-address sticky
Why have we used the first command switchport mode access and does it disable DTP ?
Step 8: Enable interface fa0/12 and generate some traffic between the switch and the router.
The connection between the switch and the router should be up/up use the show interface to verify this.
fa0/12
What are the default values used by the system when the switchport port-securitycommand is applied to an interface ?
Step 9: Access the CLI on the router and shutdown the interface connected to your switch.
Step 10: On the interface connected to your switch reset the MAC address to its original value.
Step 11: Enable the interface and generate some traffic between the router and the switch.
Step 12: Access the CLI on the switch and check the status of the interface connected to the router. You should now observe a down/down (err-disabled) state due to the port violation which occurred when you changed the MAC address of the router.
Step 13: Remove the switchport port-security and check you once again have connectivity between the switch and the router.
Task 3: Disable unused services.
Step 1: Access the CLI on the switch
Step 2: Run the appropriate command to view the CDP neighbours table (remember to use the American spelling)
Is CDP running?
Step 3: Disable CDP on the interface connected to the router and issue the command used in step 2.
Do you see a difference ?
Remember the default timeout value for CDP is 180 seconds.
Step 4: Enable CDP on the interface.
Step 5: Save your configuration.
Lab Answer Keys:
[sociallocker id=”4139″]
Task 1: Managing unused ports on a Switch.
Step 2: Ensure that the interface connecting your switch to your Router is enabled by using the no shutdown command, remember to be in the right configuration mode?
SW>en SW#conf t SW(config)#int fa0/12 SW(config-if)#no shut
Task 2: Using Switchport port-security.
Step 2: Identify the MAC address of the interface used to connect to your switch. What command could be used to achieve step 2 ?
R#sh int fa0/0
or
R#sh int gi0/0
Once you know the MAC address of the interface make a note of it below.
MAC Address:
Step 3: Enter the configuration mode which will allow you to change the interface parameters on Fa0/0 or Gi0/0.
R#conf t
R(config)#int fa0/0
or
R(config)#int gi0/0
Shutdown the interface and set the MAC address to the following value using these commands:
R(config-if)#Shut
R(config-if)#mac-address 0000.0C12.ABCD
Step 4: Enable the interface and generate some traffic by pinging the IP address of your switch.
R(config-if)#no shut
Step 5: Access the switches CLI.
What command could we use to check the MAC address of the attached router?
SW#sh mac-address
Step 6: While still accessing the CLI on the switch, shutdown the interface fa0/12
SW#conf t SW(config)#int fa0/12 SW(config-if)#shut
Step 7: Enable switchport security using the following commands:
SW(config-if)switchport mode access SW(config-if)switchport port-security
Why have we used the first command switchport mode access and does it disable DTP ?
Switchport port security is not supported over trunk connections NO it doesn't disable DTP
Step 8: Enable interface fa0/12 and generate some traffic between the switch and the router.
SW(config-if)#no shut
The connection between the switch and the router should be up/up use the show interface fa0/12 to verify this.
SW(config-if)#end SW#show int fa0/12
What are the default values used by the system when the switchport port-security command is applied to an interface ?
Max of 1 supported MAC address with a violation policy of shutdown
Step 9: Access the CLI on the router and shutdown the interface connected to your switch.
R(config)#int fa0/0
or
R(config)#int gi0/0 R(config-if)#shut
Step 10: On the interface connected to your switch reset the MAC address to its original value.
R(config-if)default mac-address
or
R(config-if)no mac-address
Step 11: Enable the interface and generate some traffic between the router and the switch.
R(config-if)no shut
Step 12: Access the CLI on the switch and check the status of the interface connected to the router. You should now observe a down/down (err-disabled) state due to the port violation which occurred when you changed the MAC address of the router.
Resetting the violated port
SW(config)#int fa0/12 SW(config-if)#shut SW(config-if)#no shut
Step 13: Remove the switchport port-security and check you once again have connectivity
between the switch and the router.
SW(config-if)#no switchport port-security
Task 3: Disable unused services.
Step 2: Run the appropriate command to view the CDP neighbours table (remember to use the American spelling)
SW#sh cdp nei
Is CDP running? YES
Step 3: Disable CDP on the interface connected to the router and issue the command used in step 2.
SW#conf t SW(config)#int fa0/12 SW(config-if)#no cdp enable
Do you see a difference ? YES
Remember the default timeout value for CDP is 180 seconds.
Step 4: Enable CDP on the interface.
SW(config-if)#cdp enable
Step 5: Save your configuration.
SW(config-if)end SW#copy run start
[/sociallocker]
